How to manage network performance?
Learn why you should manage your organization’s computer network
Network performance management
Network performance management is a process that involves providing IT administrators with information about the network. It is based on monitoring them to anticipate problems. When failures occur concerning, for example, insufficient network capacity, the IT administrator identifies them and determines the root cause of the problem. A long-term analysis of the problem is carried out. It requires IT administrators to verify the IT network using various tools. The final step in network performance management is to repair the identified failures. This process also includes backing up network configurations made so far and automating them. Below is a diagram that graphically depicts the IT network performance management process.
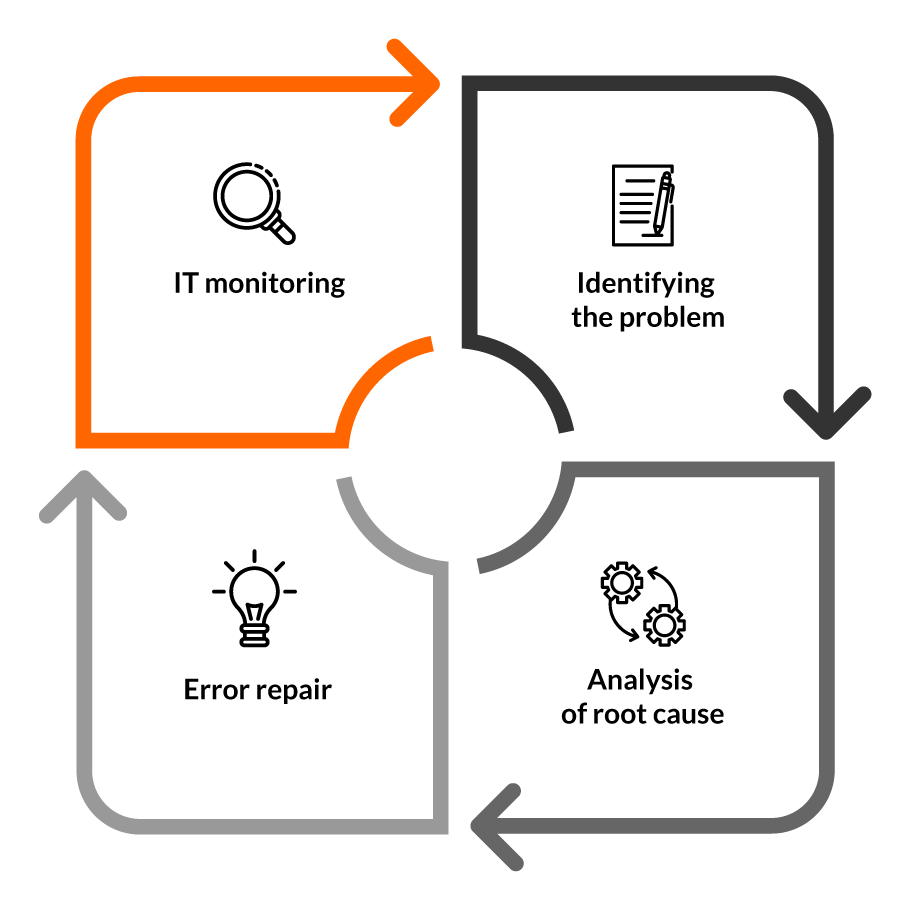
As IT infrastructure increases – monitoring and managing individual network elements becomes more complex. Its workload is also increasing, so analyzing and understanding the interdependencies between network elements requires specialized knowledge and innovative approaches. Implementing comprehensive IT systems for managing network failures and performance provides IT administrators with immediate insight into a wealth of data. This makes it possible to manage the configuration of the network, which translates into the mitigation of failures that arise and more efficient operation of both cloud and virtual infrastructure.
Benefits of network performance management
The network in an organization is prone to many errors, which can significantly affect its performance. That’s why systematic management of an organization’s network configuration is so important. This makes it possible to:
- troubleshoot network problems and proactively eliminate threats before they become apparent to the end user,
- reducing the risk of network failure based on insight into changes that occur,
- improving the quality of customer service as a result of immediate correction of errors identified in the network,
- ensuring the highest quality of service to the customer,
- streamlining the process of auditing IT resources by including all formal procedures,
- faster verification of the use of CPU, memory, disk and other parameters of devices connected to the network,
- effective bandwidth management.
Network performance management in the eAuditor system
Monitoring of network traffic with the eAuditor system is done through the network scanner. Its operation involves analyzing the company’s computer network. On this basis, all devices connected to the network, specified during the scanner’s configuration, are identified. When irregularities related to network functioning are identified, the software sends an immediate notification to the IT administrator. The information contained therein concerns the type, date and status of the device in question.
This makes it possible to react quickly to emerging network errors and eliminate them immediately. Network device monitoring also provides support for the SNMP protocol, allowing the IT administrator to check, among other things, information about devices such as switches and ports – identifying which are free and which are busy, etc. The system also makes it possible to monitor infrastructure resources such as ports running computer applications, instant messaging or peer to peer applications, among others. On this basis, it is possible to carry out an inventory of IT equipment, as the scanner provides information on IP addresses and network adapters (MACs).
5 benefits of network performance management with eAuditor
1. monitoring of the entire network environment with a single system.
2. Any way of scanning the network depending on the client’s preference (manually, by schedule or using DHCP requests).
3. Quickly leveling network problems and detecting unauthorized devices on the network.
4. Create a view of the entire network using network maps and automatically make backup copies.
5. view network data in real time.




