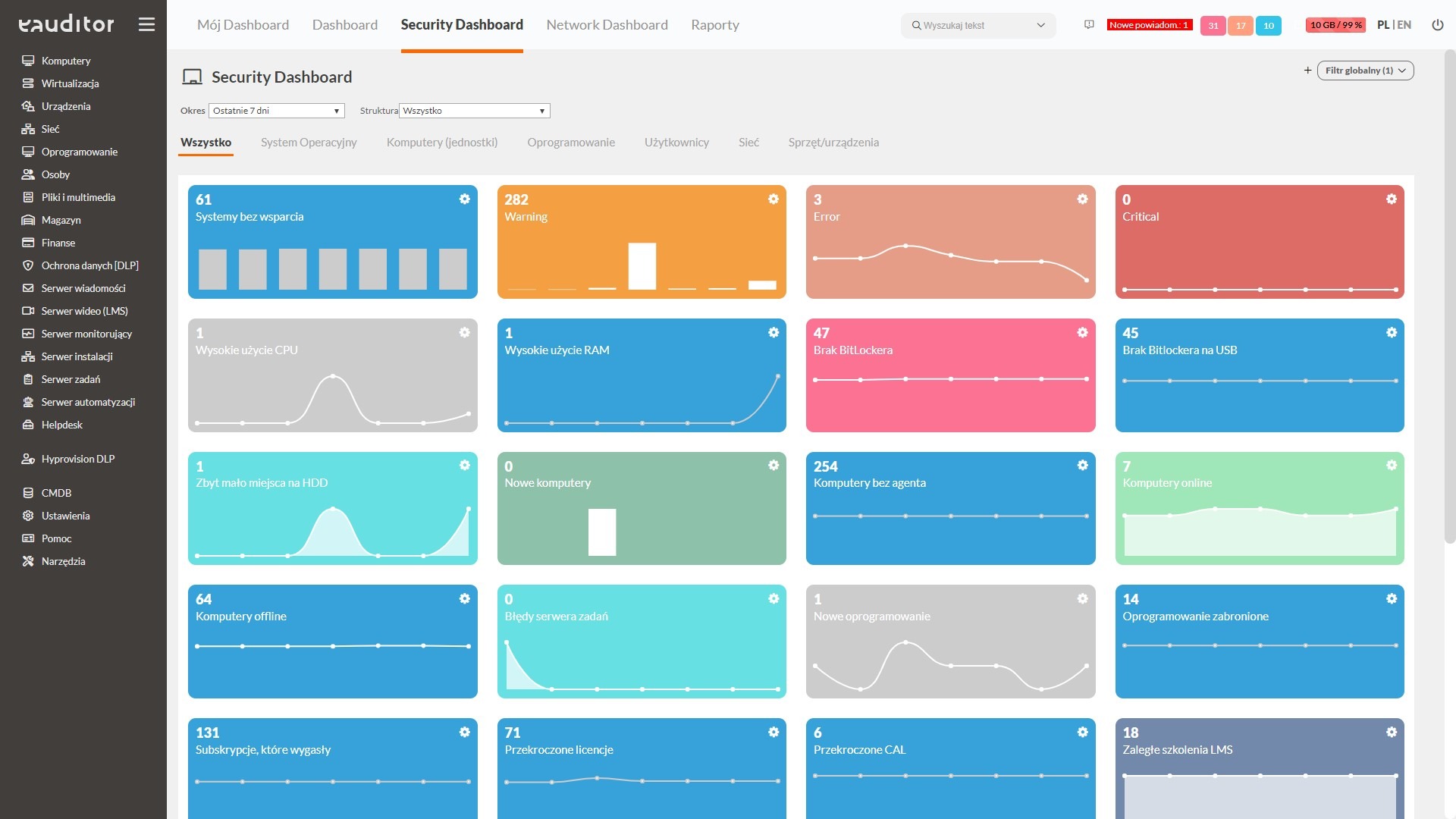
IT security
- Analysis of key SOC indicators
- Remote BitLocker encryption
- Blocking access to websites and processes
- USB blocking
- Application blocking
- Two-factor authentication
What is IT security?
IT security is closely related to the estimation and control of emerging risks and threats in an organization. It is a set of issues related to guaranteeing consistency, confidentiality and security in the circulation of information in IT systems. This makes it possible to verify installed systems and equipment for compliance with specifications and applicable laws. In addition, comprehensive protection of IT infrastructure and activities undertaken by employees affects the security of key resources, including data.
Why provide IT security?
Adequate IT security prevents many negative consequences that can affect the operation of an organization. Lack of adequate IT infrastructure security can lead to infected IT systems, for example, due to accidental or intentional actions by employees. Such behavior can trigger hacking attacks and compromise the company’s security. The scope of processed information is so wide that its loss can have severe consequences for the entire organization. Regardless of the type of business and the size of the company, the IT administrator should take special care to protect them.
Benefits of using a system to ensure IT security
Securing data in the organization
With the use of appropriate procedures, it is possible to protect against incidents leading to leakage of personal data.
Improving the efficiency of processes and operations
By ensuring adequate IT security in the organization, it is possible to regulate issues related to employee access to specific resources. In addition, monitoring user privileges allows you to maintain consistency of duties performed and responsibilities assigned within the organization.
Counteracting incidents
Adequate IT security monitoring allows you to detect gaps in data protection and prevent potential incidents. Preventing incidents is therefore much less severe in its consequences than allowing attacks such as ransomware.
Cost savings – appropriate IT security software can prove to be a much smaller expense than the consequences associated with, for example, a data leak. According to analysts, the consequences of IT security negligence incidents will become increasingly severe.
Caring for the positive image of the organization
Disruptions negatively affect a company’s image. They also cause a decrease in trust among customers, which also translates into significant financial losses.
Elements included in the provision of IT security
IT security includes activities related to the protection of data stored on all devices in an organization. This is one of the key processes implemented by IT departments, as data leakage can cause serious consequences and disrupt the continuity of business processes. In addition, protection also applies to running processes and visited websites preventing from, for example, pishing. The most important elements of implementing this process should be identified as: