Remote firewall management
- Firewall status monitoring
- Remote firewall control
- Network traffic control
- Instant attack prevention.
Remote firewall management
Protecting against unwanted third-party activity and malware is the cornerstone of navigating the Web safely these days. One of the most important tools that helps with this is the firewall, or firewall.
Remote firewall management is a key component of network security management. It allows administrators to configure, monitor and manage the firewall from anywhere, which is important especially for distributed networks or cloud infrastructures.
Remote firewall management allows you to:
Real-time monitoring of firewall status
Remote firewall management allows administrators to monitor firewall status in real time and quickly identify unwanted traffic on the local network. Easy access in the web console allows for quick response from anywhere and elimination of potential threats.
- information about the status of the firewall
- information about active rules
- implementation status
- information about the protocols and ports used
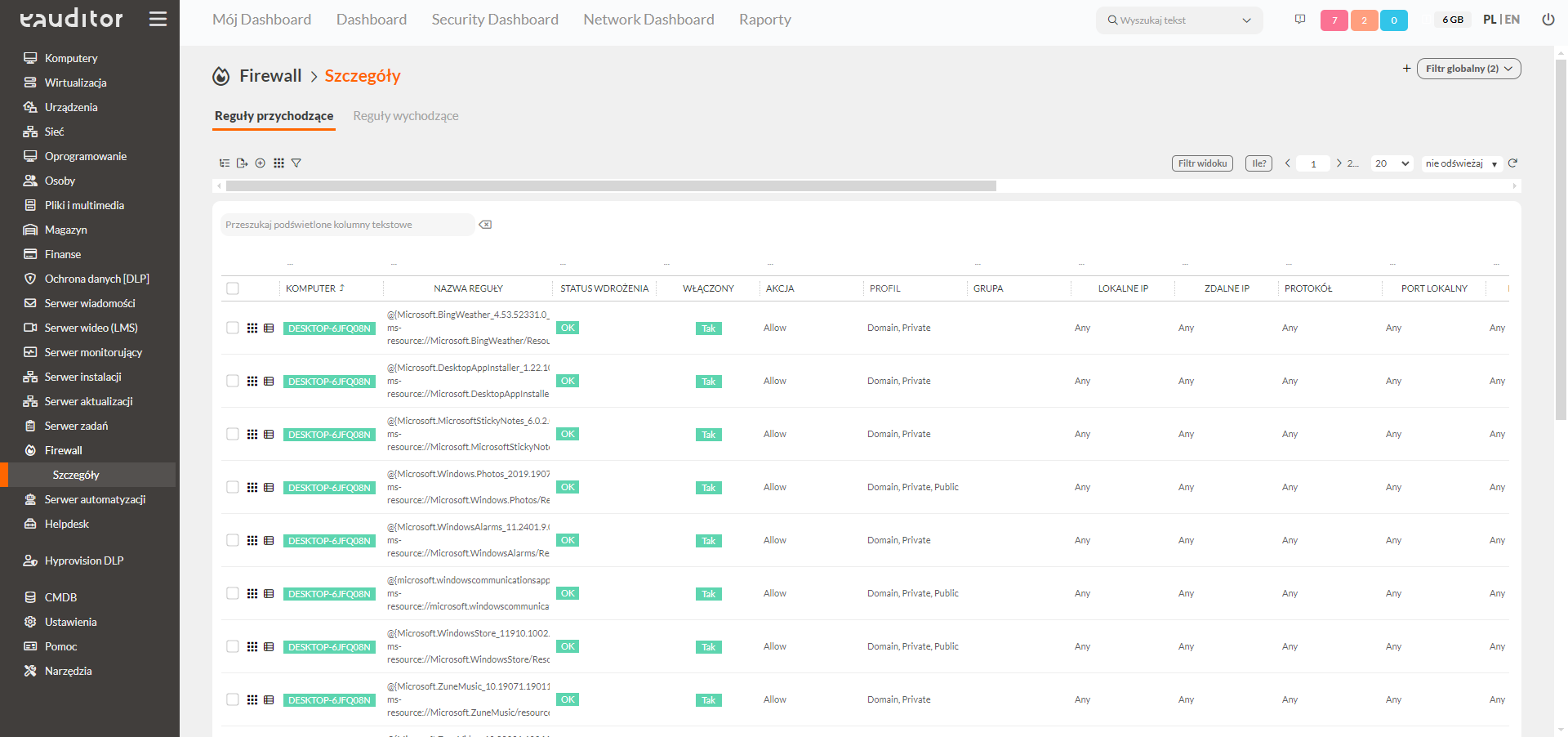
Remote control of the firewall on any computers
Remote firewall management process, allows administrators to easily configure local network security on multiple devices from different locations. This way, we can be sure that we can respond quickly to potential threats if necessary.
- possibility to define groups of computers for the applied rule
- Filter support for faster selection of target devices
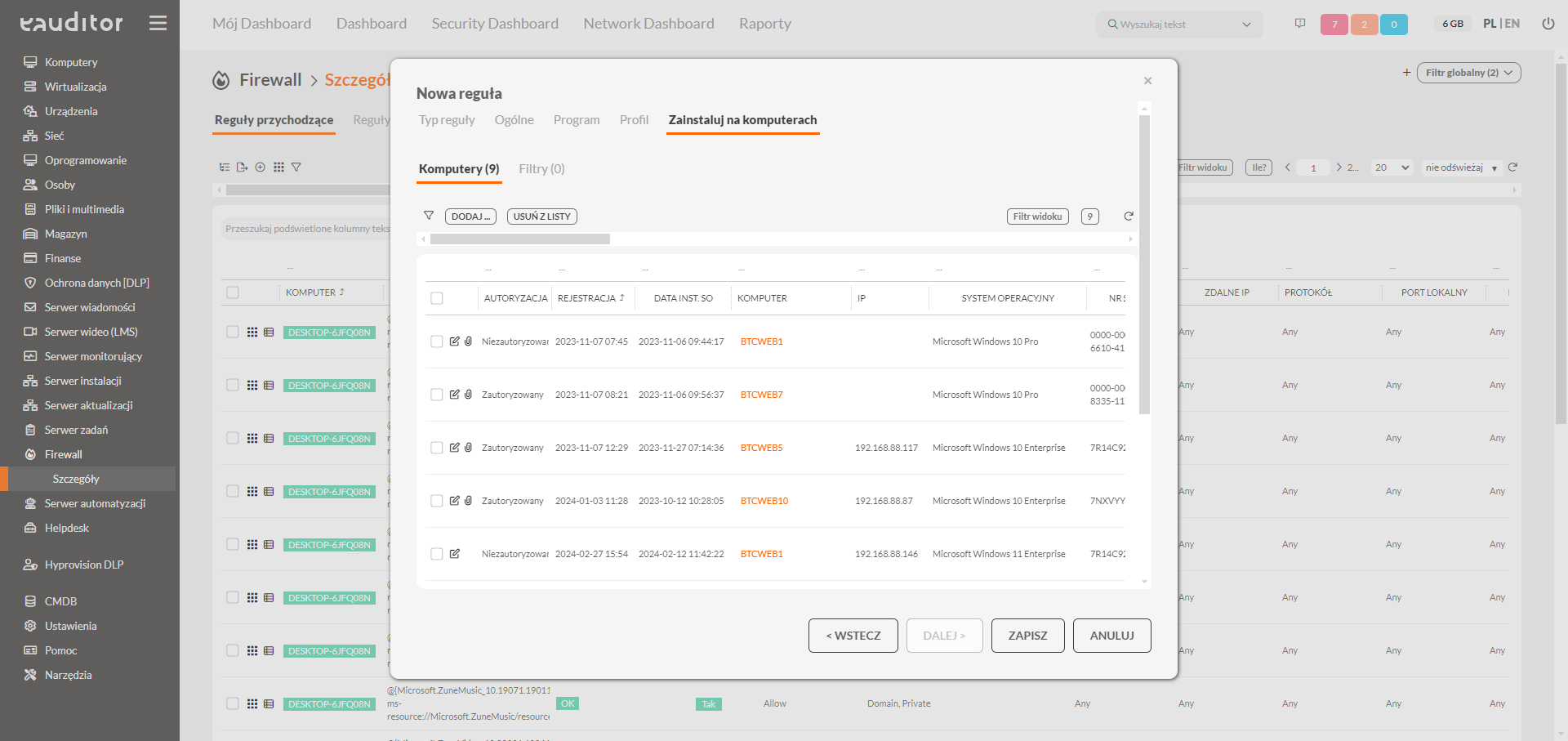
Define and manage complex firewall rules from a central administration panel
A central point from which we can define firewall rules is a key aspect that allows us to monitor and act against threats to our network in an organized manner. This gives us greater control and insight into what wickets in our infrastructure are still open to unwanted visitors.
- defining inbound and outbound rules for software and ports
- defining names and rule descriptions
- managing the state of the rule
- ability to define rules for domain, private and public network profiles
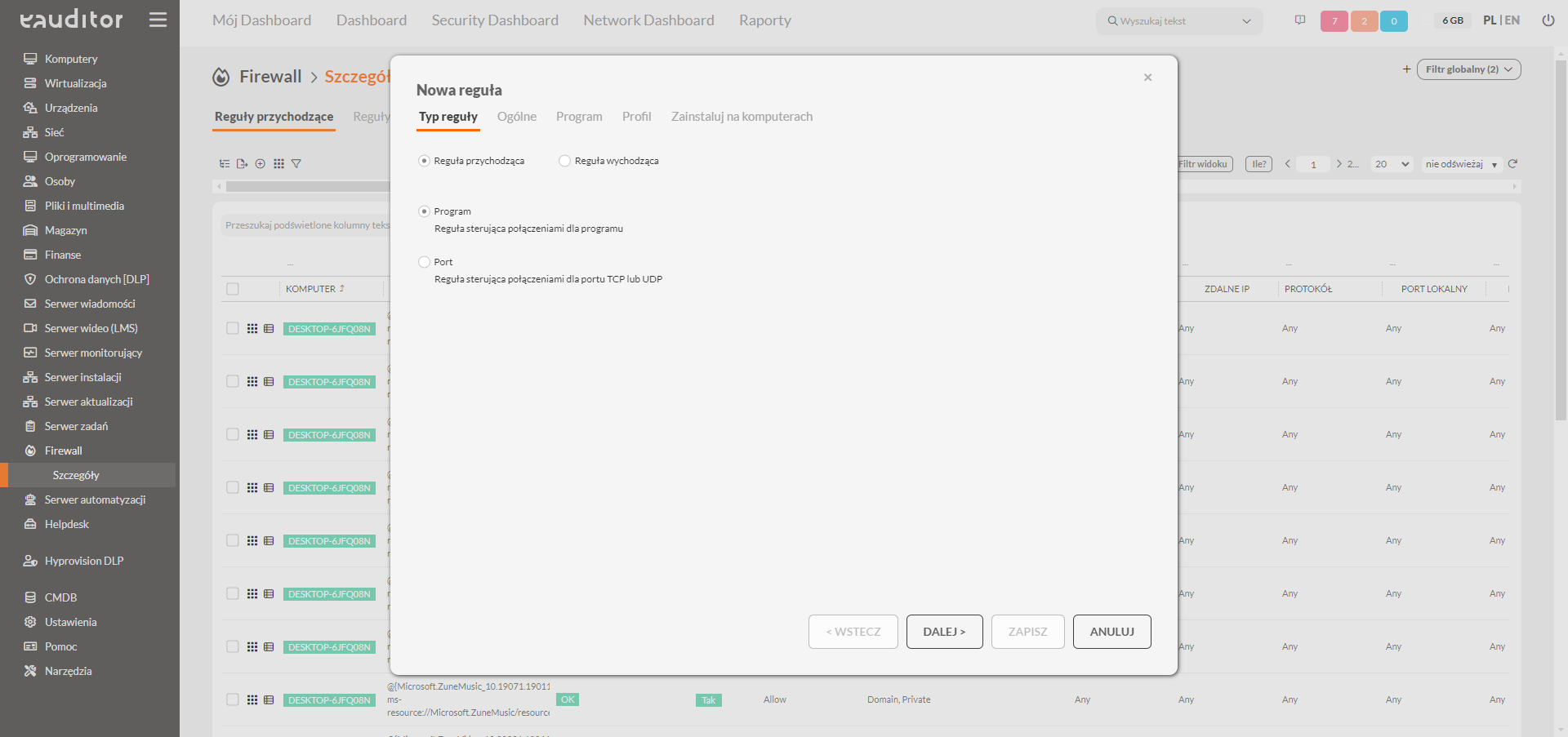
Quickly identify and respond to potential threats
The reaction time we have from the detection of a threat is crucial when we want to minimize the risk. That’s why central points that enable rapid and simultaneous response across the entire infrastructure perform well in the area of prevention.
Network traffic control
In the eAuditor system, this functionality is responsible for ensuring the security and performance of computer networks. It includes monitoring, managing and regulating the flow of data across the network to ensure compliance with security policies and optimize network performance. Effective control of network traffic requires the use of a variety of tools and techniques, as well as continuous monitoring and adaptation of network security policies to changing conditions and requirements of the organization. This helps ensure both the security and efficiency of computer networks.
Immediate prevention of attacks
An effective network security strategy is nothing more than immediate prevention of attacks. It involves responding quickly to detected threats and taking immediate action to stop an attack or minimize its effects. By employing these methods and continuously improving network security strategies, organizations can minimize the risk of attacks and the impact of potential security incidents. However, it is also important to continuously monitor and analyze activities to adapt the security strategy to changing threats and network environment.
