Email monitoring
- Email Monitoring (Outlook)
- Audit of Sent Emails
- Record of Headers (Subjects)
- Outgoing Mail
Table of contents
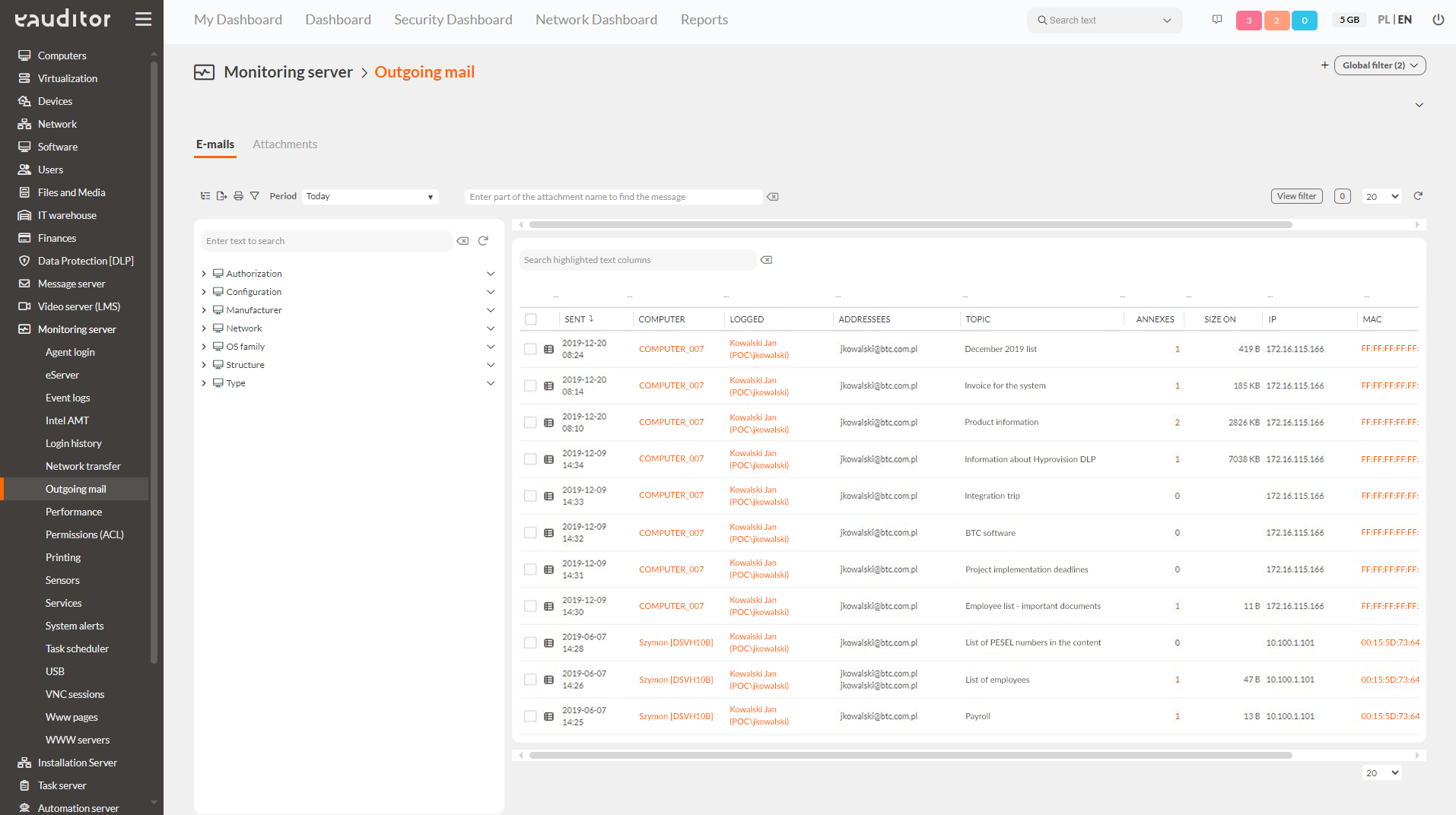
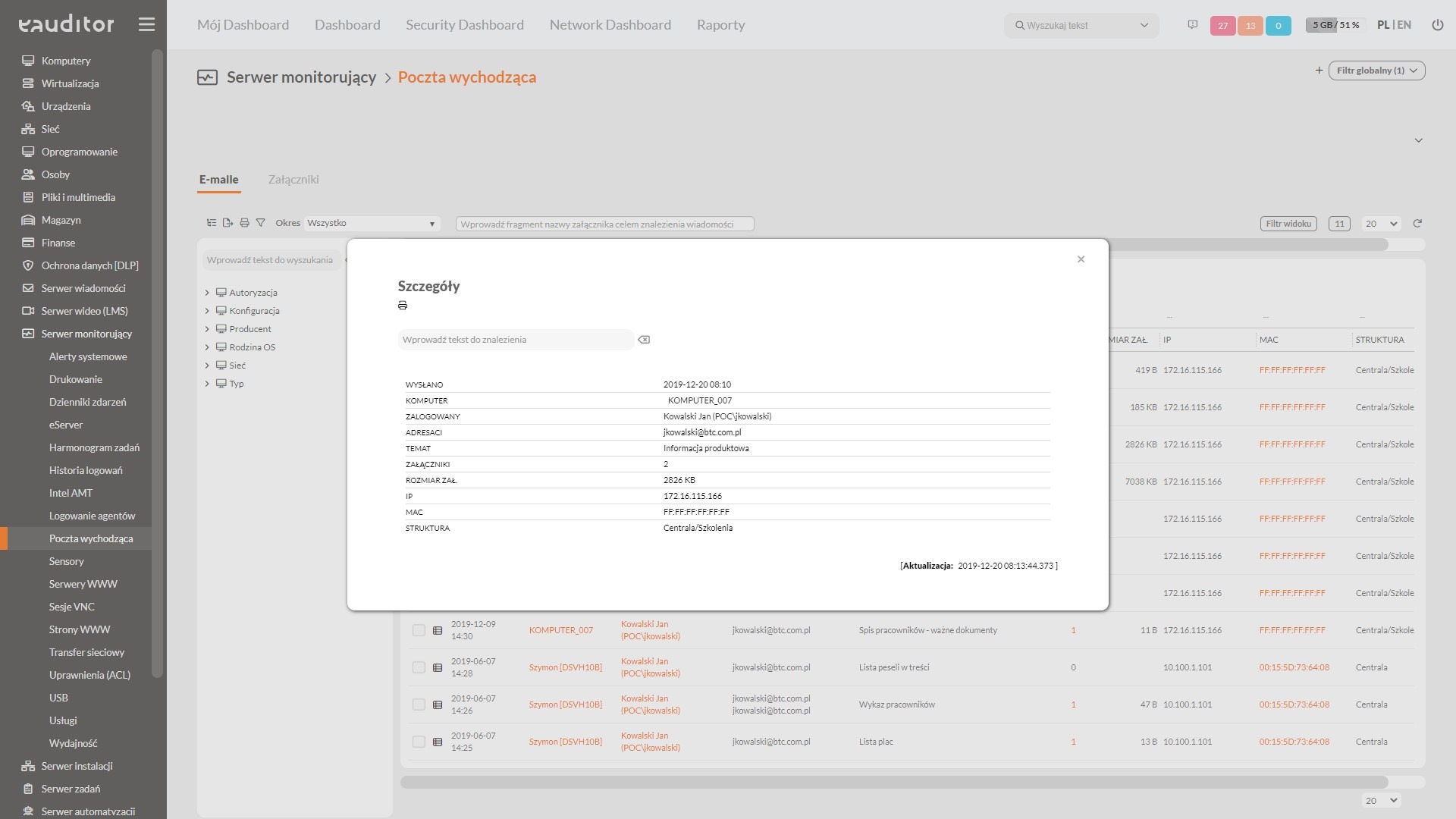
What does email monitoring look like?
With the eAuditor system, the administrator can monitor the outgoing mail of his employees using Outlook. It will quickly and efficiently audit sent mails (only message subjects, message content is not monitored) along with attachments. This provides insight into the size, extension and titles of documents attached to messages. This makes it possible to prevent employee abuse of inappropriate use of business e-mail. Records of headers (subjects) also make it possible to detect irregularities in the titling of business e-mails.
Using the e-mail monitoring function makes it possible to
- verifying correct use of e-mail,
- verifying compliance with security procedures for sent attachments,
- detecting irregularities in the titling of business e-mails,
- verify the activities of users using e-mail so that they comply with the organization’s implemented security policies.
Regulations for the use of e-mail
- notify the employee of the monitoring of messages, the purpose, the scope of monitoring, and the method of implementation,
- implement appropriate procedures (regulations, policies) establishing in detail the rules of monitoring,
- apply the means and scope of monitoring appropriate to the situation,
- comply with the requirements related to not violating the secrecy of correspondence and other personal property of the employee (Article 223 of the Labor Code of June 26, 1974).
Benefits
Want to learn more about monitoring? Watch the video and see what other possibilities the eAuditor system offers in this area