Device monitoring
- Monitoring Network and Local Printers
- Computer Monitoring
- Hard Drive Monitoring
- USB Monitoring
Table of contents
Device monitoring
Device monitoring is an important step not only in terms of controlling the use of resources, but also ensuring security. IT managers are required to ensure that all equipment available in the organization complies with numerous legal regulations (RODO, KRI, ISO). These documents impose an obligation to monitor IT equipment in the organization. Inadequate administration of equipment can lead to violations of regulations and procedures. By monitoring IT resources, it is possible to identify unauthorized events and activities, as well as unauthorized access to resources – computer, software or data. Monitoring can be done through eAgents installed on computers. The administrator then downloads the MSI package and configures the eAgent. An ID is then randomly generated and the service connects to the eServer. Monitoring of IT resources is then done by scanning location data, thanks to a network scanner. The data obtained is limited to basic device information, which is more extensive for devices that return information after SNMP. Then, after clicking on the list tab, the administrator has a view of all devices imported via API, SNMP or from a file.
In the eAuditor system it is also possible to generate labels and filter devices by name, user or device type. IT hardware monitoring includes monitoring of all resources in an organization, such as computers, printers, monitors, etc. It makes it possible to verify equipment by its whereabouts. In addition, the administrator also has insight into whether the computer is online or offline. The administrator can also monitor changes in hardware performance parameters and, based on this, forecast the occurrence of a potential failure. In this way, appropriate actions can be implemented to prevent potential hardware downtime due to, for example, hardware failure.
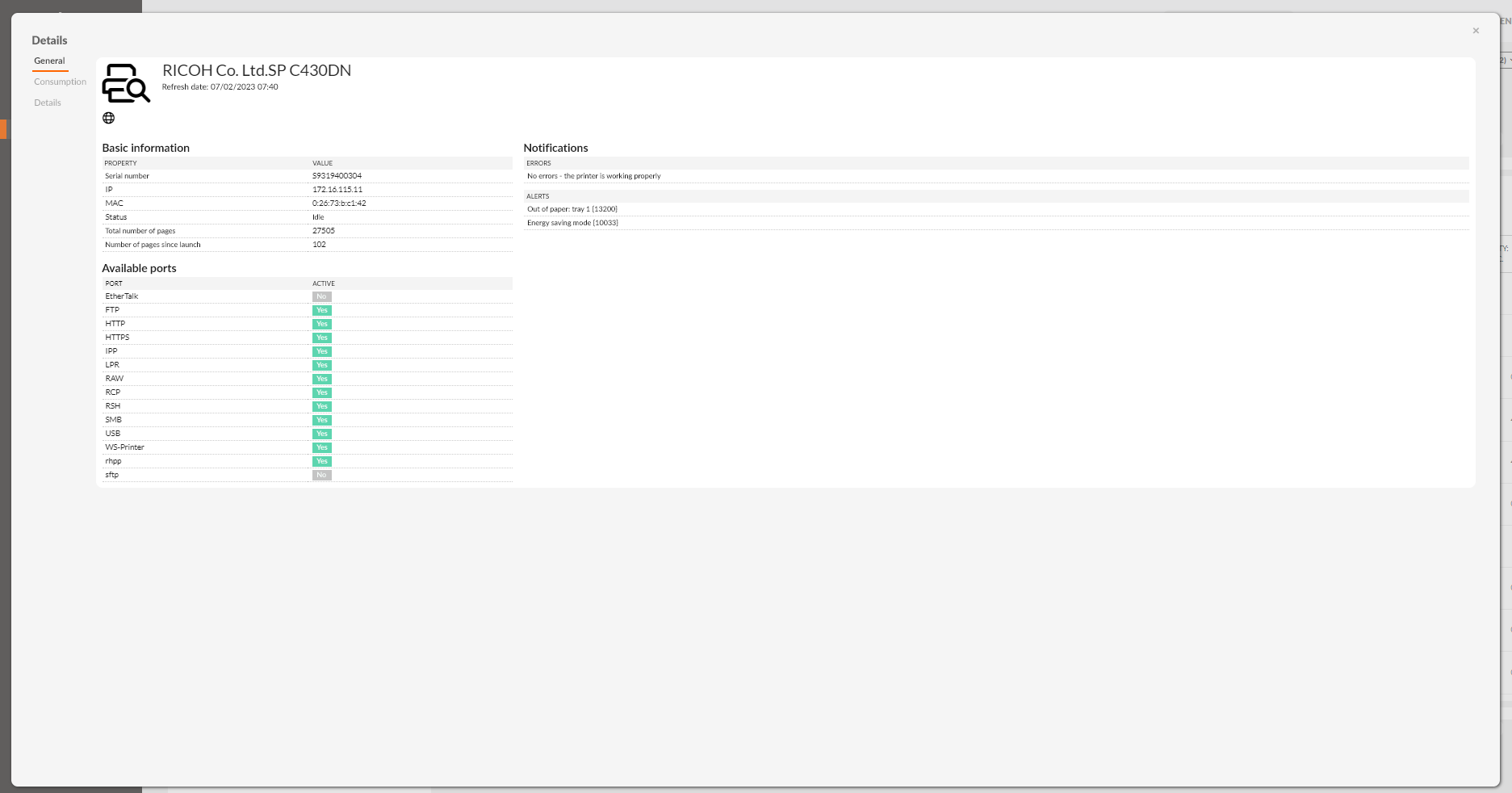
Monitoring network and local printers
The eAuditor system allows effective monitoring of all network and local printers located in the organization. The administrator can verify actual toner consumption, read information about printer alerts and statuses, as well as verify minimum, maximum and average printer service response times. This is not only a great convenience in terms of ensuring the continuous operation of printing devices, but also in terms of responding quickly to incidents that arise, so as to minimize the occurrence of any damage or failure. The administrator can monitor what files have been printed by users along with an indication of the number of pages, etc. Attributes such as inventory number, barcode, responsible person, computer set to which it belongs, etc. can be assigned to the device.
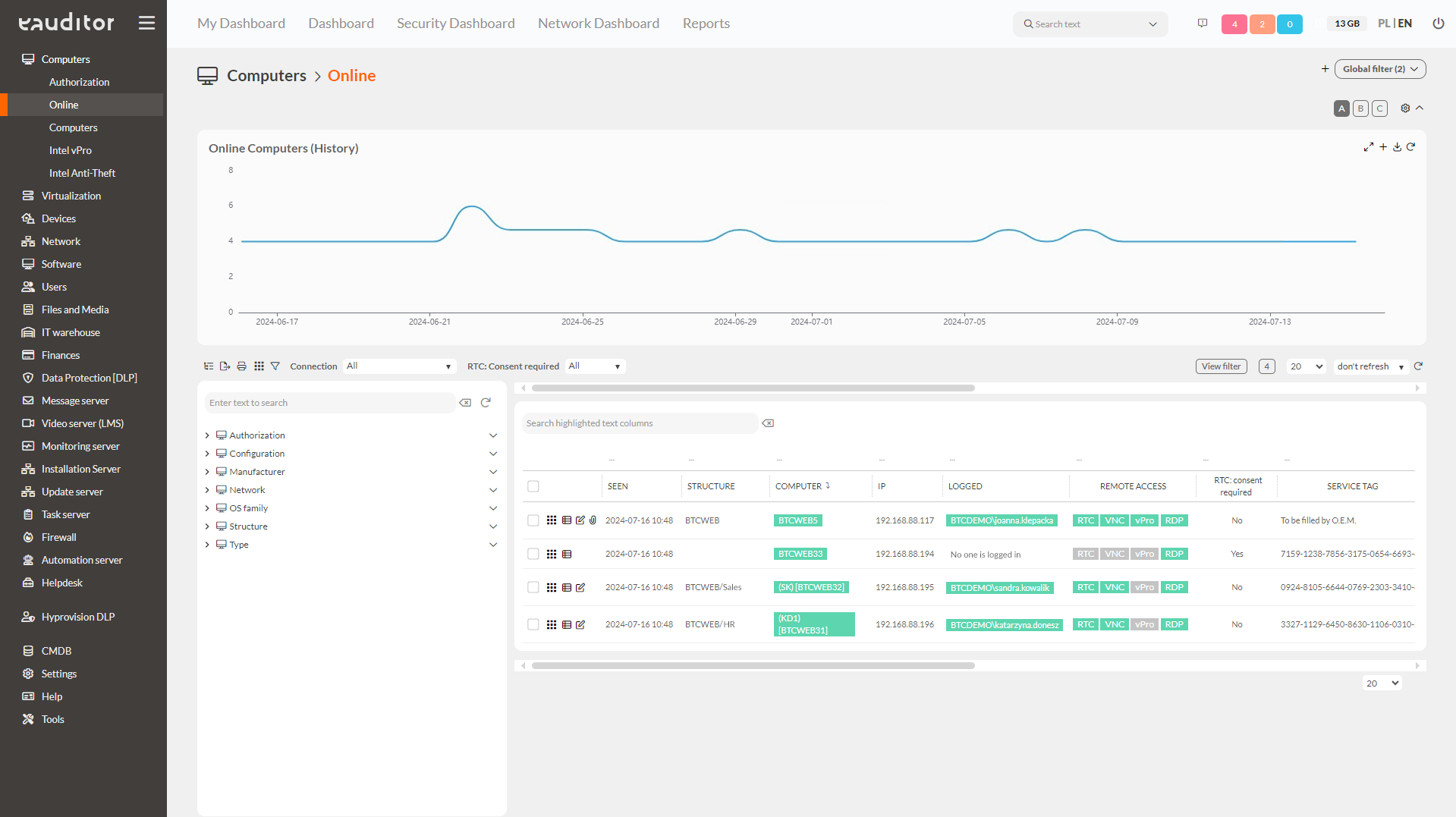
Monitoring of computers
The eAuditor system allows monitoring of computers used by employees. The administrator can verify which computers have eAgent installed and which do not. In the system, he also has an overview of all computers in the organization, along with an indication of which user it has been assigned to. It then receives information on whether the user is using the remote desktop function, for example. In addition, by clicking on a particular computer, the administrator goes to the so-called, detailed tab, where he can get information about the processor used, BIOS, memory used, etc., but also identify operating systems or applications used by the employee. In addition, he can see, among other things, the working time, printouts made, web pages viewed, as well as available permissions on a particular device.
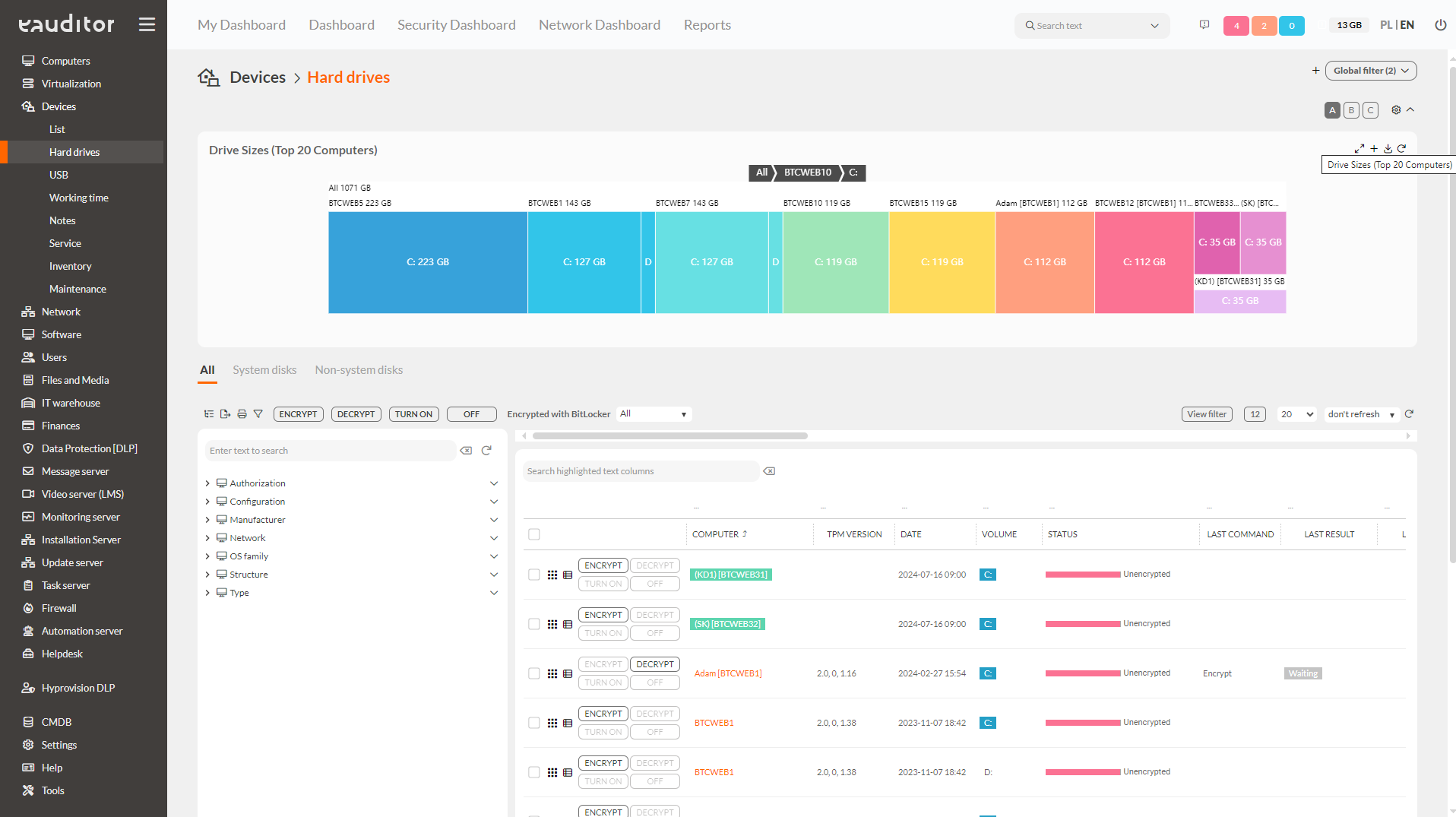
Hard disk monitoring
The administrator has access to a view of the disks with a full view of all the most important information. He can monitor whether a drive has been encrypted using Microsoft BitLocker and verify messages about recent errors, drive size or the extent of free space on the drive, among other things.
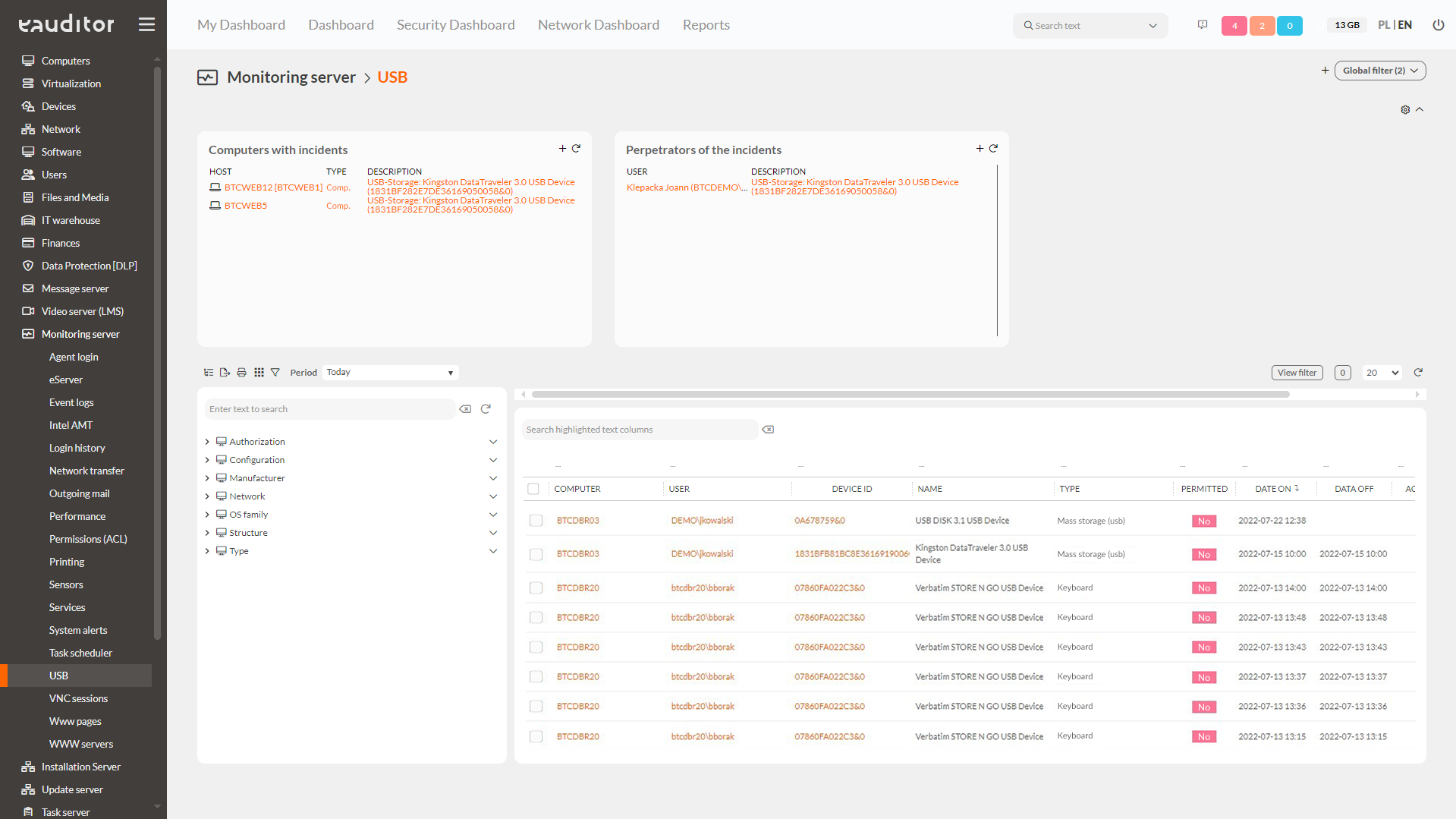
USB monitoring
The system allows you to monitor the USB taking into account the following information:
- name,
- USB type,
- encryption status,
- presence of the USB in the so-called white lists,
- the last use of the USB on a given computer,
- the last use of the USB by a user.
The administrator can also set interactive widgets according to his preferences. They will be immediately available in the console after entering the appropriate tab. They then inform, for example, about the breakdown of memory types.
Benefits
Want to learn more about this functionality? Read the article “Effective monitoring of devices on the network”