Monitoring of software and operating systems
- Monitoring of operating systems
- Monitoring of applications
- Monitoring of packages
- Monitoring of running processes
Table of contents
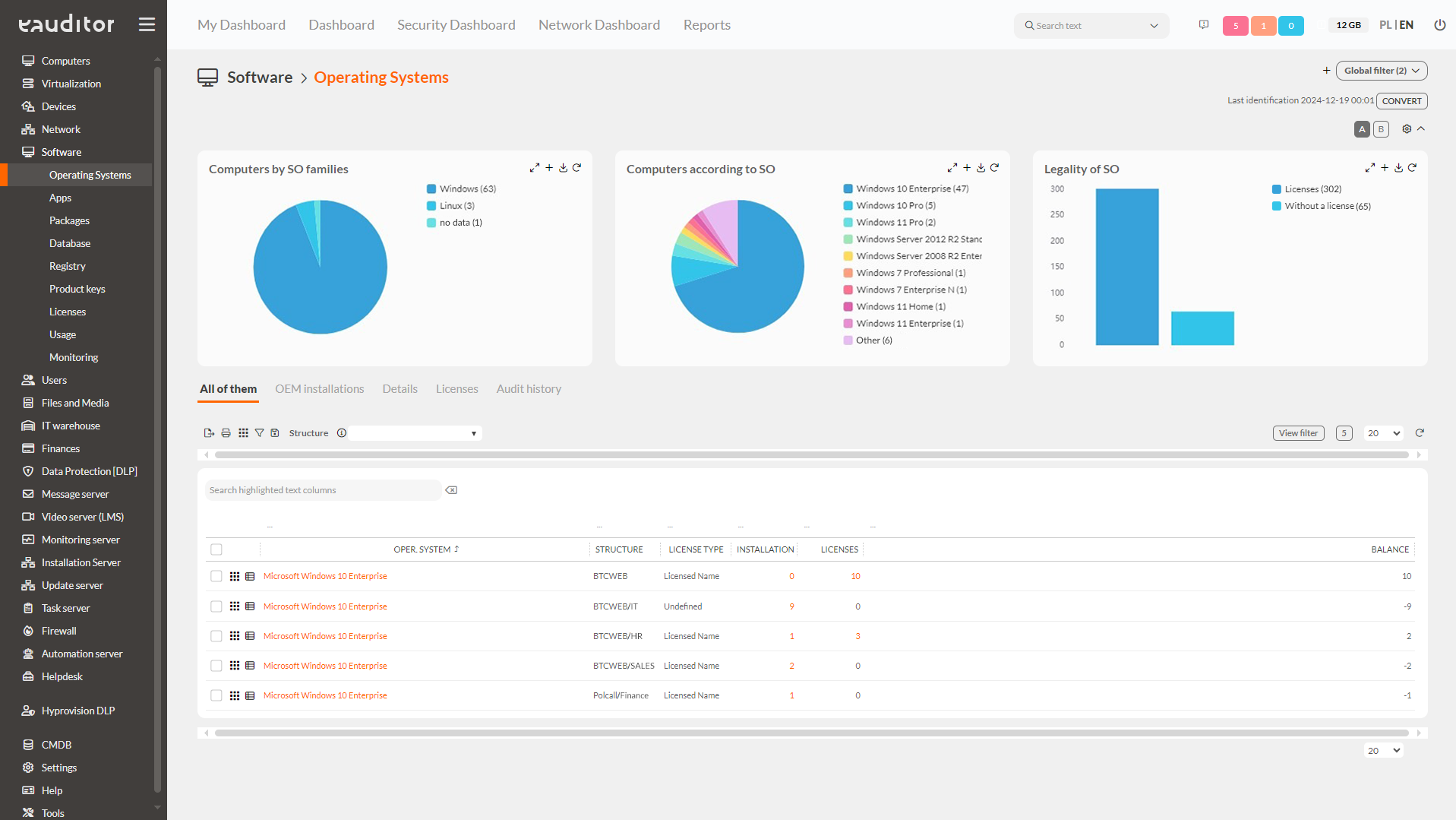
Monitoring of operating systems
With eAuditor, it is possible to monitor operating systems for a number of factors. eAuditor determines the legitimacy of operating systems by indicating that their licenses are up to date. In addition, interactive widgets show, among other things, the percentage of computers according to the operating system installed and the summed number of all types of operating systems. It is worth noting that in eAuditor it is possible to add any of the available widgets to the My dashboard tab according to your own preferences. This can depend on what is important to the administrator at the time. When the administrator clicks on a specific computer name, he can view its detail tab. In the tab that appears, he can check exactly whether this system has been authorized and when its registration was performed. eAuditor also allows them to be monitored for:
- types of licenses that are currently used in the organization, e.g. enterprise, OEM,
- organizational structure indicating in which departments the operating systems are currently used,
- the number of operating system installations made in the infrastructure.
The eAuditor software also makes it possible to monitor licenses including purchase date, number, unit price and expiration date. This allows the administrator to systematically verify the operating systems installed on computers, in one place, with one tool. This greatly facilitates cost management in the organization. In the console it is also possible to view the history of software legality audits carried out. It is also possible to compare any historical “audit” with another.
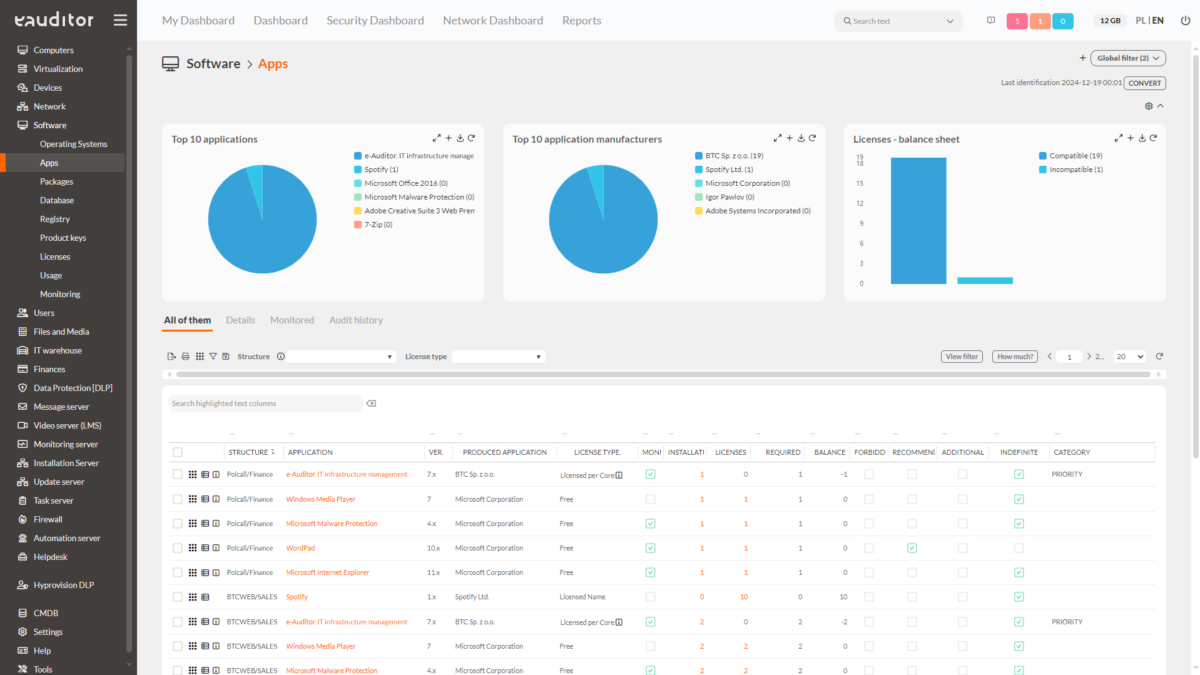
Application monitoring
The eAuditor system also makes it possible to monitor the applications that users use. It monitors their activity, degree of use and time of effective use. The administrator can freely filter the applications to be monitored with the indication of the computer or the period during which the user used it. He has an insight into the productivity of an application, i.e. the ratio of all its startup time to the user’s actual activity time. It can also monitor their category and the start and end times of any activity in it.
In the eAuditor system, in order to monitor application activity, you must first prepare the appropriate eAgent configuration. Then substitute the prepared configuration for eAgnet on selected computers that the administrator wants to monitor in this regard. After enabling this functionality, the eAuditor system will start generating a list of all running applications and processes. The system will record processes both in terms of the time they were started, the time they were stopped, and the total time they used a given application. In addition – by analyzing the extent of use of a given application – the system will indicate how long the user had the application running and how long he actively used it. What’s more, if the selected application is opened in multiple windows, eAuditor will show which windows were active and for how long. Using the Word application as an example, we will see which documents are open and how long the user has been using them. We will get the same result when monitoring all other applications.
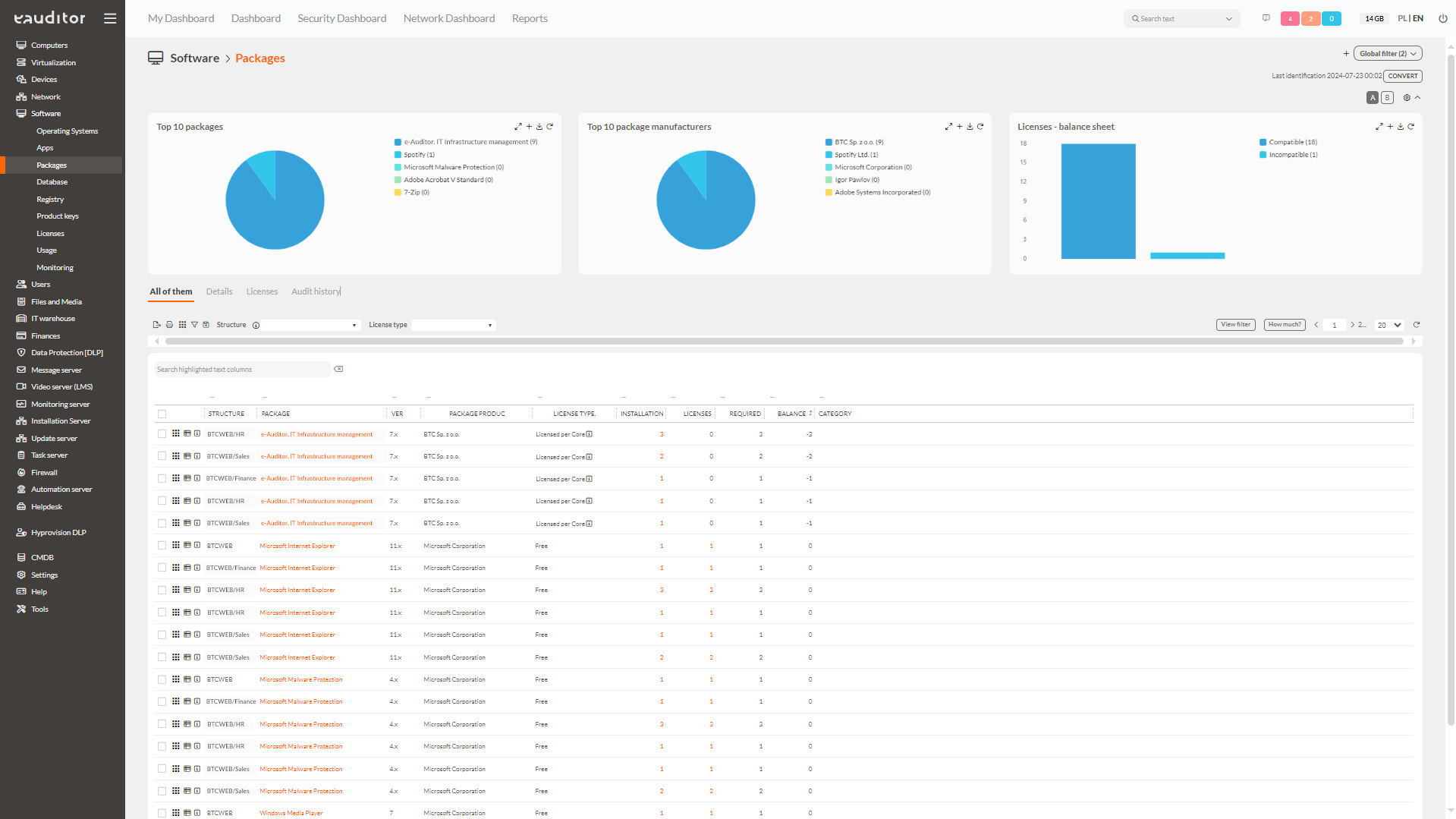
Package monitoring
The eAuditor system allows monitoring of packages, i.e. applications from a single vendor. The administrator can freely filter packages based on the organization’s structure or license type. He or she then has an overview of information about application packages, including manufacturer, version, etc. The administrator can also monitor the expiration time of application package licenses. In the console it is also possible to view the history of audits performed and compare them to historical ones.
The eAuditor system provides widgets which will present selected information about application packages. They can be about, for example, application vendors, which users in a given organization use most often. In addition, after clicking on a selected package, the administrator has a view of the structure used by users.
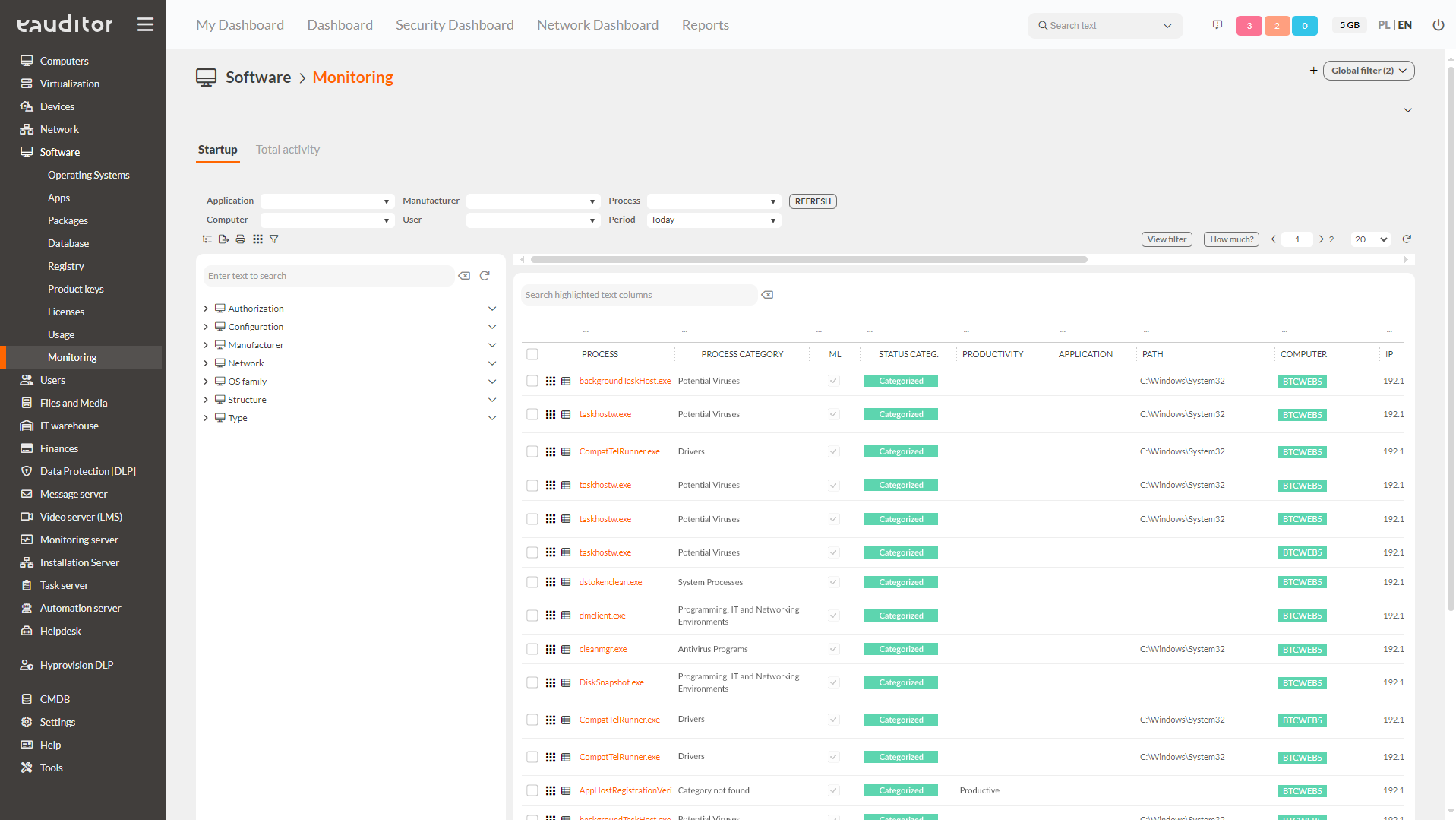
Process classifier
The eAuditor system also enables monitoring of running system processes using artificial intelligence. This functionality has many benefits that affect among other things:
Increasing security
Assessing employee productivity with Process Classifier, using artificial intelligence, significantly impacts the continuity of an organization’s operations. BTC Process Classification minimizes the risk of attacks and monitors processes and applications run by users in real time. This allows the administrator to react much faster to impending threats and effectively protect corporate data from attacks. BTC Process Classification also allows specific actions to be taken In addition, the use of advanced artificial intelligence algorithms allows faster and more efficient assignment of categories for individual processes.
Improve the efficiency of employees’ work
Using the process classifier, the administrator will effectively check the efficiency of employees’ work and verify the productivity of the applications they use. In this way, it is possible to monitor the work of employees. This allows you to eliminate so-called time distractions, making the employees’ work more efficient.
Artificial intelligence
The process classifier has been equipped with artificial intelligence in order to:
- automate the creation of a database with information about processes, their categories along with productivity and safety assessments,
- real-time synchronization with the database of classified processes in the datacenter,
- automatically updating the categories after a certain period of time.
AI implementation in the process classifier works based on the following steps:
- Starting the process classification procedure (sending the process name to the search engine and to dedicated pages containing information about processes),
- The code of the page is downloaded for later analysis (downloading the content of the page),
- The page code is cleaned of unnecessary data, such as repeated words and HTML tags,
- After the code is cleaned of redundant components, words (keywords) that determine the nature of the process will be left (Identification of keywords that determine the type of application to which the process under study is assigned),
- Repeated keywords are assigned to categories based on the dictionary, and the number (saturation) of words within each category is determined,
- The process is assigned to the category that is identified as the most likely.
The main features that characterize this functionality are:
- API usage,
- speed of operation,
- continuity of operation 24/7.
- 12 categories – process safety assessment – process productivity assessment – process blocking according to selected criteria.
BTC AI
- Processes are classified based on their actual content and assigned to one of 21 categories, achieving an efficiency of more than 85%.
- The high efficiency of classification is due to the artificial intelligence algorithms used and the database of keyword patterns built within each category.
- The catalog of classified processes and applications is constantly expanded and available in the cloud
- The standard speed of the classifier is > 10 processes/sec.
Benefits
Want to learn more about this functionality? Read the article “How to effectively monitor the activity of running applications?”