Anonymization and pseudonymization in IT
Anonymization and pseudonymization guarantees data security, so it works well in IT systems
Data protection in IT
The introduction of RODO has changed the IT world and ushered in a number of new challenges. Properly processing, storing, or ensuring the privacy of personal data has become a major responsibility in the technology industry. To a greater or lesser extent, most organizations have had to subordinate their systems to the newly applicable rules for securing personal data. One way to help ensure data security and privacy is anonymization and pseudonymization.
What is anonymization?
Anonymization is the permanent removal of data that makes it impossible to identify a specific person. It involves the removal of personal data information from the database, with the result that there is no way to determine which person a specific document relates to. Importantly, the process is irreversible, so once it is done, the administrator loses the technical ability to restore the data to the system. After anonymization, the data becomes fully anonymous, thus significantly reducing the risk of data leakage. The anonymization process means that an unauthorized person who will have access to the database will not gain access to the personal data, but only to the anonymized version.
What is pseudonymization?
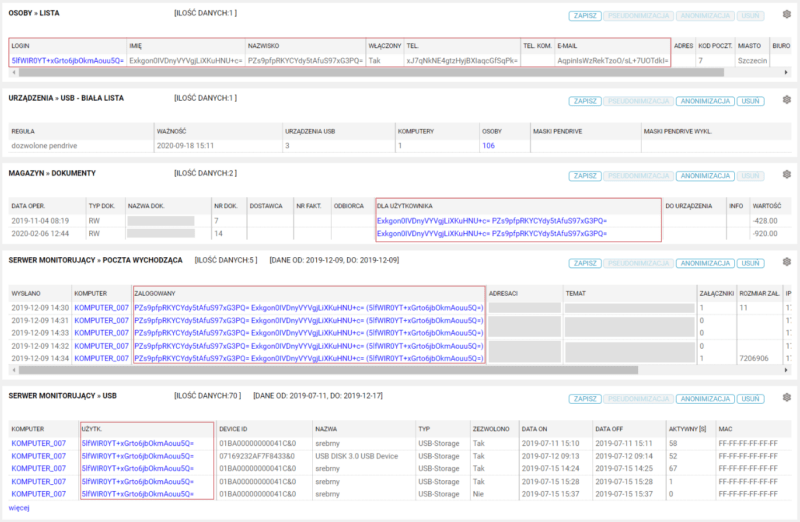
Pseudonymization of data is one method of anonymization with the difference that it is a reversible process, and is a much weaker security measure for personal data. It involves altering them in such a way as to make it possible to identify the person to whom they belong. Identifying data is replaced with pseudonyms, which can be, for example, a string of numbers or letters. Pseudonymization ensures the anonymity of the user, while maintaining the correlation of the various data as a whole.
Anonymization and pseudonymization in eAuditor
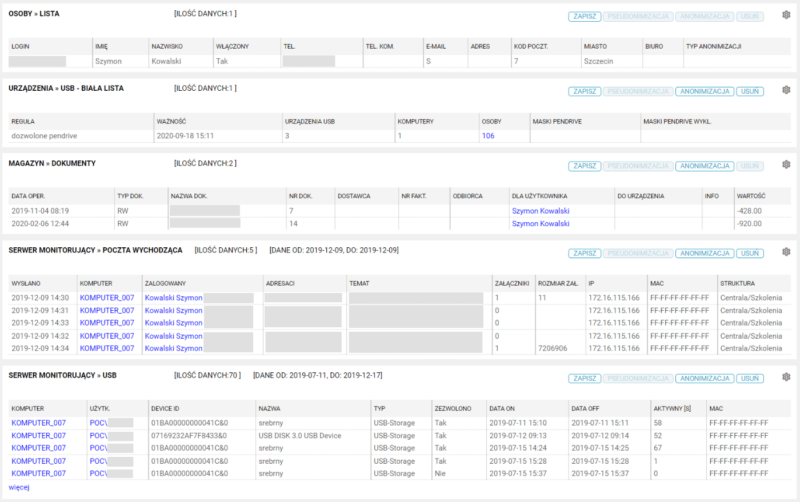
Huge amounts of data are processed in IT systems every day. They concern private personal data of users, or information about their activities. When processing and storing such data, software must meet the appropriate requirements and guarantee security in terms of confidentiality. The eAuditor system has both a personal data anonymization and pseudonymization option.
When using the anonymization process, users’ personal data, such as their name, email address, or user ID are irreversibly transformed so that it is impossible to identify the person to whom the data belongs.
Using pseudonymization, users’ personal data is replaced with pseudonyms, such as a string of numbers or letters, so that without a special key it is impossible to decipher to whom the data belongs. Importantly, the pseudonymization process can be reversed.