IT system security in companies
In his book ‘Practical Unix and Internet Security,’ Simson Garfinkel and Gene Spafford state, “A computer system is secure if its users can depend on it, and if the software performs its intended function.”
Today, the security of IT systems in companies worldwide has become a top priority. In an ideal IT reality, computer systems should be professionally secured. Unfortunately, real-world statistics paint a different picture. In 2023, there were 11% more cyber attacks compared to the previous year. Despite the increasing number of systems designed to protect data, security vulnerabilities continue to emerge, posing significant challenges for software developers.
Is there a way to combat data breaches? Can we guarantee that entered data will remain with us permanently and won’t be accessed by unauthorized individuals? Below, we present contemporary challenges in IT security faced by IT software creators and innovative protection strategies.
Security threats to information systems: 5 challenges for IT
Below, we present 5 key challenges faced by IT system creators:
1. Protection against hacking attacks
Ransomware attacks and phishing are the most common threats to IT security. Ransomware locks or encrypts files on devices, while phishing aims to extract information. Protecting data in IT systems from these attacks is a priority, as they can lead to unauthorized access to sensitive categories of data, such as personal or financial information.
2. Protection against cybersecurity attacks
Advanced attacks, also known as multi-vector attacks, are becoming increasingly complex. Barracuda Networks experts forecast that while email remains a fundamental vector for many advanced threats, these attacks will become more intricate, utilizing multiple infection methods. Implementing advanced protection strategies is essential, such as event monitoring, antivirus solutions for IT systems, and IT security training.
3. Automatic software updates
Unupdated software poses a significant risk, as hackers can exploit known security vulnerabilities. It’s important to pay special attention to this and have the ability for automatic updates of all software on the computer.
4. Training in threat awareness
Employee Training in Data Protection Awareness, especially in the context of social engineering threats, is crucial. Employees should be aware of the risks associated with phishing, confidentiality breaches, and other threats.
5. Secure access to data during remote work
Remote monitoring and management tools make it safe to work from anywhere. IT systems utilizing remote device monitoring and management tools enable a swift response to hacking attacks, thereby protecting organizations from intentional or accidental data leaks.
Protection strategies – eAuditor software
Enhancing the security of information systems requires, above all, awareness of threats and the use of appropriate tools. One innovative solution is the eAuditor system, which provides a range of functionalities to enhance security in IT systems:
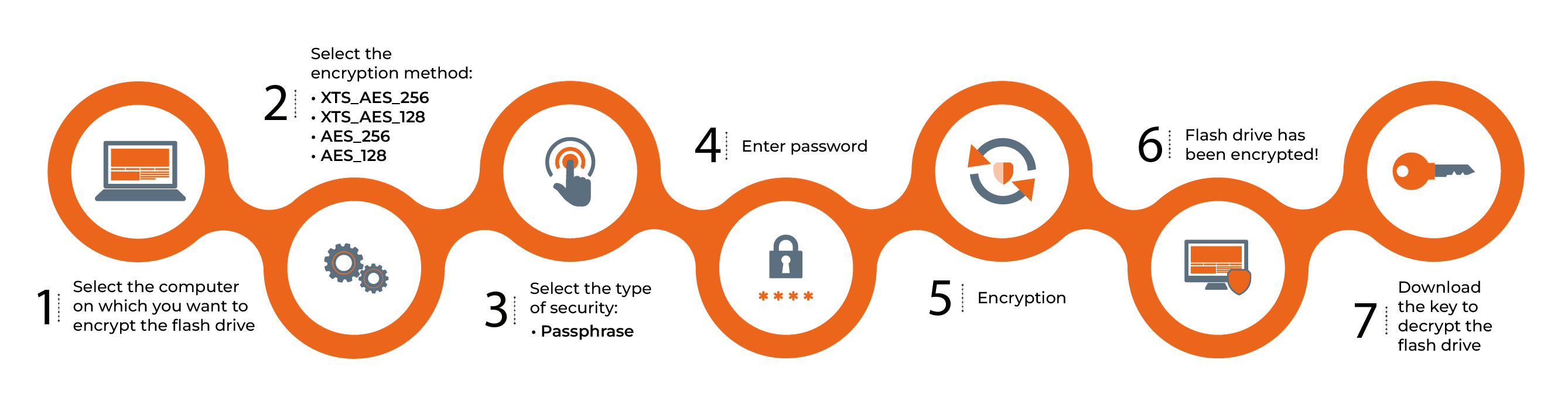
BitLocker remote encryption:
This tool is built into the Microsoft operating system. BitLocker is one of the many functionalities seamlessly integrated with the eAuditor system, thanks to its open API. The BitLocker feature is based on an encryption algorithm, securing access to sensitive data on portable devices and internal drives. This means that BitLocker protects data from unauthorized access, for example, in the event of a lost USB drive.
Network device monitoring:
With the eAuditor system, it is possible to monitor devices and ports within a specific network. Any abnormalities detected in the monitored devices can trigger automatic notifications to the IT administrator. The system allows for scanning an IP range, providing information on the detected devices from this scan/process. This data is collected through the operation of the eAgent service on a given device, within the parameters specified in the eAgent configuration. Network device monitoring streamlines the process of tracking IT resources and responding to emerging errors, thereby enhancing the cybersecurity of IT systems.
Blocking access to websites and launched processes:
BTC Website Classification has a real impact on IT security. The classifier analyzes the URLs used by employees and checks whether their category is safe. Through classification and providing information about the security (or lack thereof) of a website, the administrator can react more quickly and protect the organization from intentional or accidental data leaks, even in the case of remote work. BTC Process Classification enables the swift and seamless classification of system processes and applications. The classifier is also equipped with a range of mechanisms that automatically reject incorrect processes. Additionally, its engine is located in the Data Center and is supported by a scalable set of servers, ensuring unlimited solution performance.
Software asset management (SAM):
Software auditing is the process of assessing and verifying compliance with the requirements of this standard. Through auditing, programs used in the organization, including licenses, versions, and other relevant information, will be identified. eAuditor has a database of public patterns regularly updated by the BTC technical team. Thanks to these patterns, eAuditor can currently recognize over 4000 applications and packages based on various criteria such as versions, manufacturers, or license types. This allows for effective monitoring and ensuring the accuracy of the gathered data. Additionally, through software management, the audit detects any discrepancies, such as unauthorized software or license violations.
Learning management system (LMS):
LMS (Learning Management System) is an advanced system that enables employee training through videos posted in the public and private console. Automation in this case allows for the renewal of training. This means that, within a specified period, training will renew in the employee’s panel, and the user will need to retake it to receive an updated certificate. With these key features of the system, employees gain greater awareness of emerging threats and learn how to respond to situations related to phishing, confidentiality breaches, or other dangers.



