Vulnerability scanning – the foundation of your organization’s cyber security
On how eAuditor supports IT protection, automatically detects threats and facilitates incident management
Why scan for vulnerabilities in installed software?
In today’s digital world, IT infrastructure security is a priority for every organization. One of the key elements of protection is systematic vulnerability scanning of installed software. Modern IT environments are increasingly complex, and with them the risk of cybercriminals exploiting security vulnerabilities is growing.
What are vulnerabilities and why are they a threat?
Vulnerabilities are weaknesses in software that can be exploited to launch attacks, such as taking control of a system, stealing data or disrupting services. Because of constant updates and the release of new versions of applications, it is often difficult to keep up to date and respond to these threats.
Like eAuditor helps detect vulnerabilities?
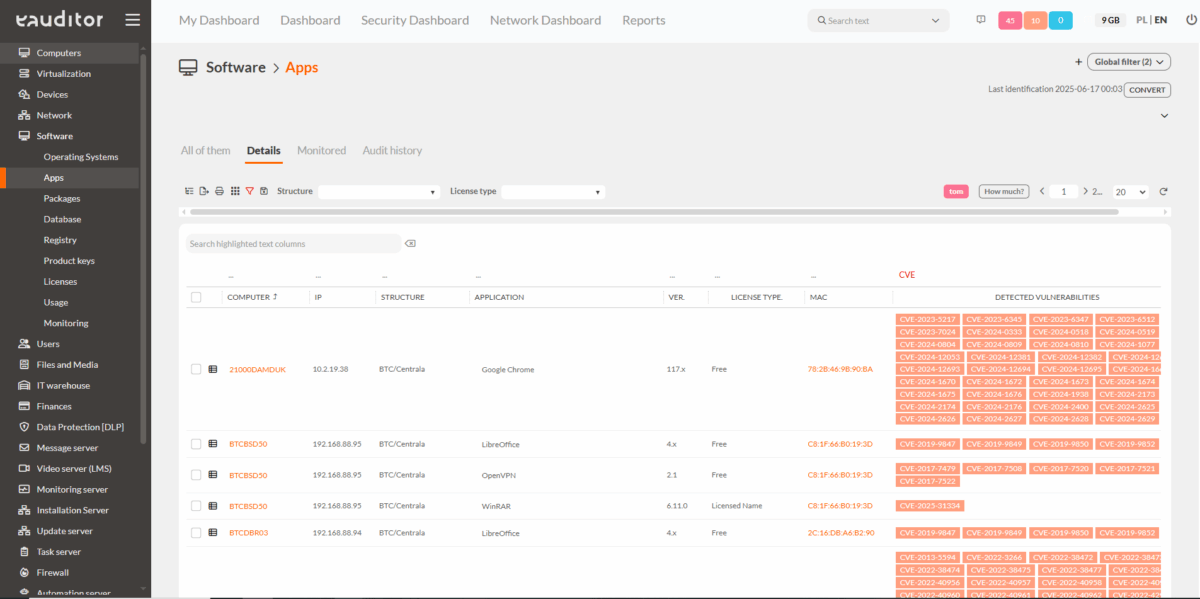
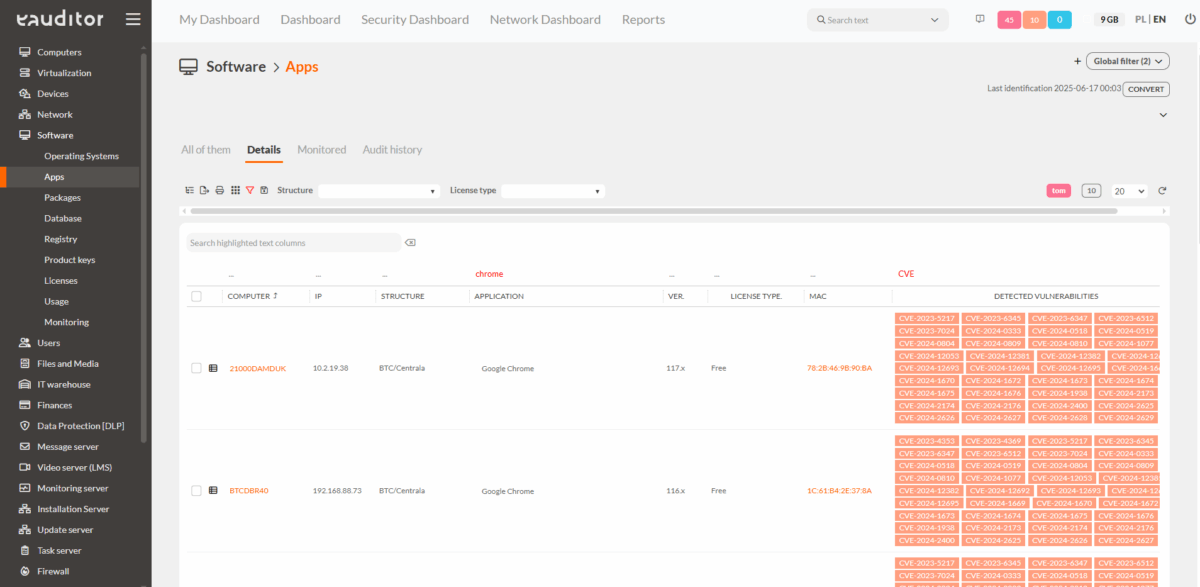
The eAuditor system introduces innovative vulnerability detection functionality based on patterns of installed software and correlation of CVE (Common Vulnerabilities and Exposures) databases. This allows users to:
- Automatically identify vulnerable elements of your infrastructure,
- Instantly respond to detected threats by recording them as incidents in the eHelpDesk system,
- Monitor security status with detailed reports generated by eAuditor.
Benefits of regular vulnerability scanning
- Proactive protection against attacks
Early detection of vulnerabilities enables rapid implementation of corrective actions before the threat is exploited. - Reducing business risks
Knowing the state of software security helps minimize potential financial and reputational losses. - Meeting regulatory requirements
Regular vulnerability scanning and reporting is often a requirement of standards such as ISO 27001 or RODO. - Optimization of incident management processes
Integration with the eHelpDesk system allows efficient tracking and resolution of security issues in one place.
Summary
Implementing systematic vulnerability scanning of installed software is an indispensable part of a modern IT security strategy. Thanks to the solution eAuditor, which automatically identifies threats and supports the incident management process, organizations gain an effective tool to protect their infrastructure from growing cyber threats.