Vulnerability management
- Automatic gap detection
- Integration with CVE databases
- Scanning the entire IT infrastructure
Spis treści
Vulnerability management
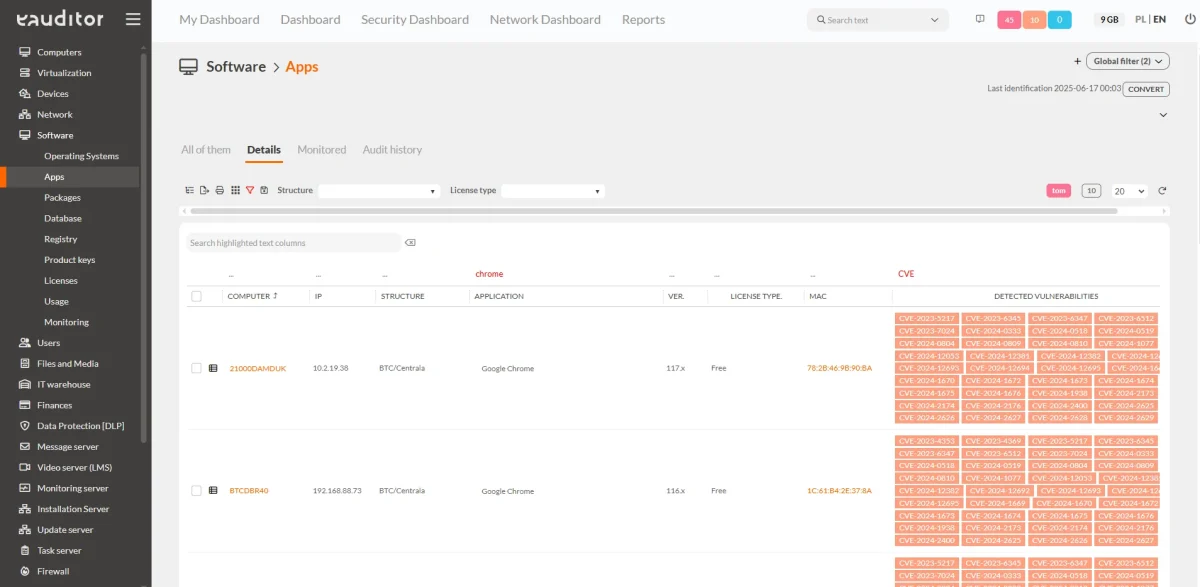
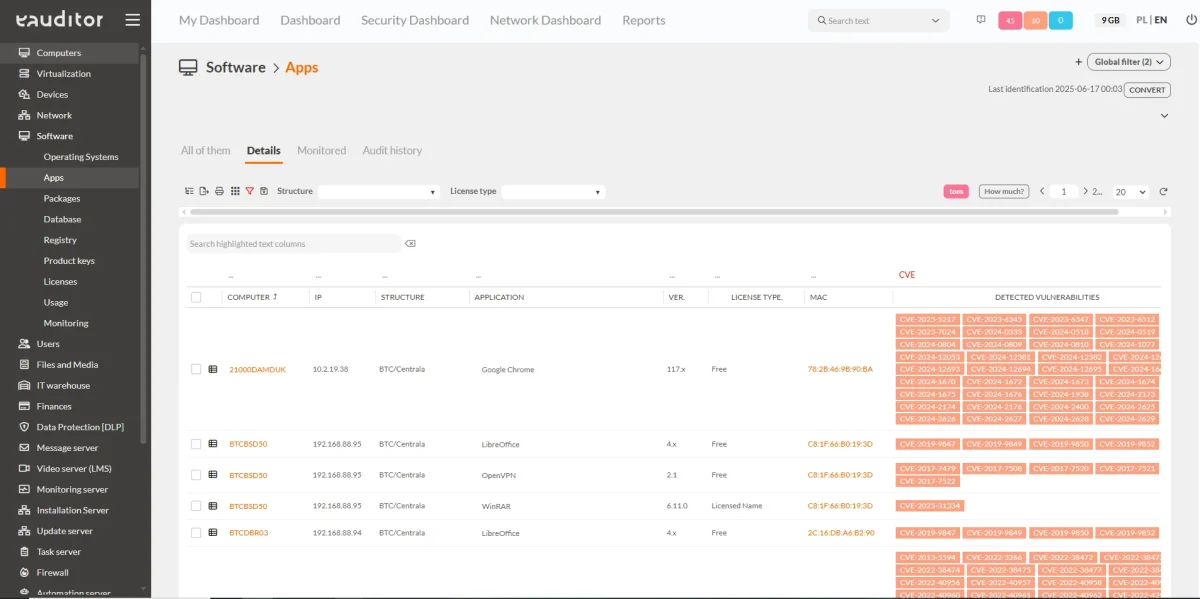
Vulnerability management in the eAuditor system allows you to identify threats in installed software and IT devices in real time. The system automatically detects security vulnerabilities by analyzing the collected data and comparing it with global vulnerability databases such as CVE (Common Vulnerabilities and Exposures).
This functionality enables continuous monitoring of the security status of the IT infrastructure, supporting administrators in responding quickly to detected risks.
The eAuditor system uses data from software inventory and application versions to correlate with up-to-date information on known vulnerabilities. As a result, the user receives a clear list of detected vulnerabilities along with the threat level.
Scanning and identification
Vulnerability management in eAuditor includes:
- Automatically scans software for known vulnerabilities,
- Comparison of results with CVE databases,
- Risk level assessment and prioritization of risks,
- Automatic creation of incidents in the eHelpDesk system,
- Reporting with the ability to filter by device, vulnerability type or criticality level.
This allows IT administrators to manage security effectively, and all activities are centrally documented.
Benefits
With its vulnerability management functionality, eAuditor provides comprehensive support in protecting your IT infrastructure. Automatic scanning, ongoing updating of threat databases and integration with other system modules make security management simpler and more effective.