eAuditor system network scanner
Learn how the network scanner in eAuditor enables scanning of active devices, services and ports.
Table of contents
1. What is a network scanner and how does it work?
2. Network scanner functionalities
3. Network scanning
4. Deleting a scanning session
5. Remote agent installation
6. Remote installation of any software
7. Adding to devices
8. History
9. Network maps
10. Scanning devices on the network
11. Scanning active services
12. Monitoring of harmful or potentially harmful services/ports
13. Building network maps
14. SNMP
15. Remote installation
16. Equipment inventory
17. Quality control of LAN connections
What is a network scanner and how does it work?
A network scanner is software that scans a computer network to find all connected devices that have an IP address that falls within the address range set during the scanner’s configuration. An example range looks like the following: 192.168.1.2 – 192.168.1.255
With this setting, the scanner will search for devices within the 253 address range.
Calling the scanning action can be done in 3 different ways:
- manually,
- using a scheduler,
- using DHCP requests – each computer that connects to the network for the first time and has DHCP service enabled on the network card, sends a broadcast information (request) to everyone on the network. In this information it asks for an IP address to be assigned, the eAuditor system scanner intercepts this request and – after an appropriate delay – launches a network scan.
How does the search work?
The scanner relies on the ICMP protocol – this is the network protocol on which practically everything in the network is based, but for the purposes of this document it is enough for us to know that thanks to it such programs as ping (checks the connection between 2 hosts) and tracert (checks the route and which routers the packet passes through) work. The network scanner uses an “ICMP Echo Request” message sent from the scanner to the host, to which the host must respond. The host here is a single address from the range set during the scanner’s configuration. If the host does not respond with an “ICMP Echo Reply” message, the scanner checks the active ports – if it detects nothing, it means that the address is free and no device is assigned to it.
The network scanner in the eAuditor system also allows scanning the ports used by computers, so we can find out what services are used by the devices in our organization. The scanner also has support for the SNMP protocol, so we can check, among other things, information about devices such as switches and the status of their ports – which are free and which are busy, etc.
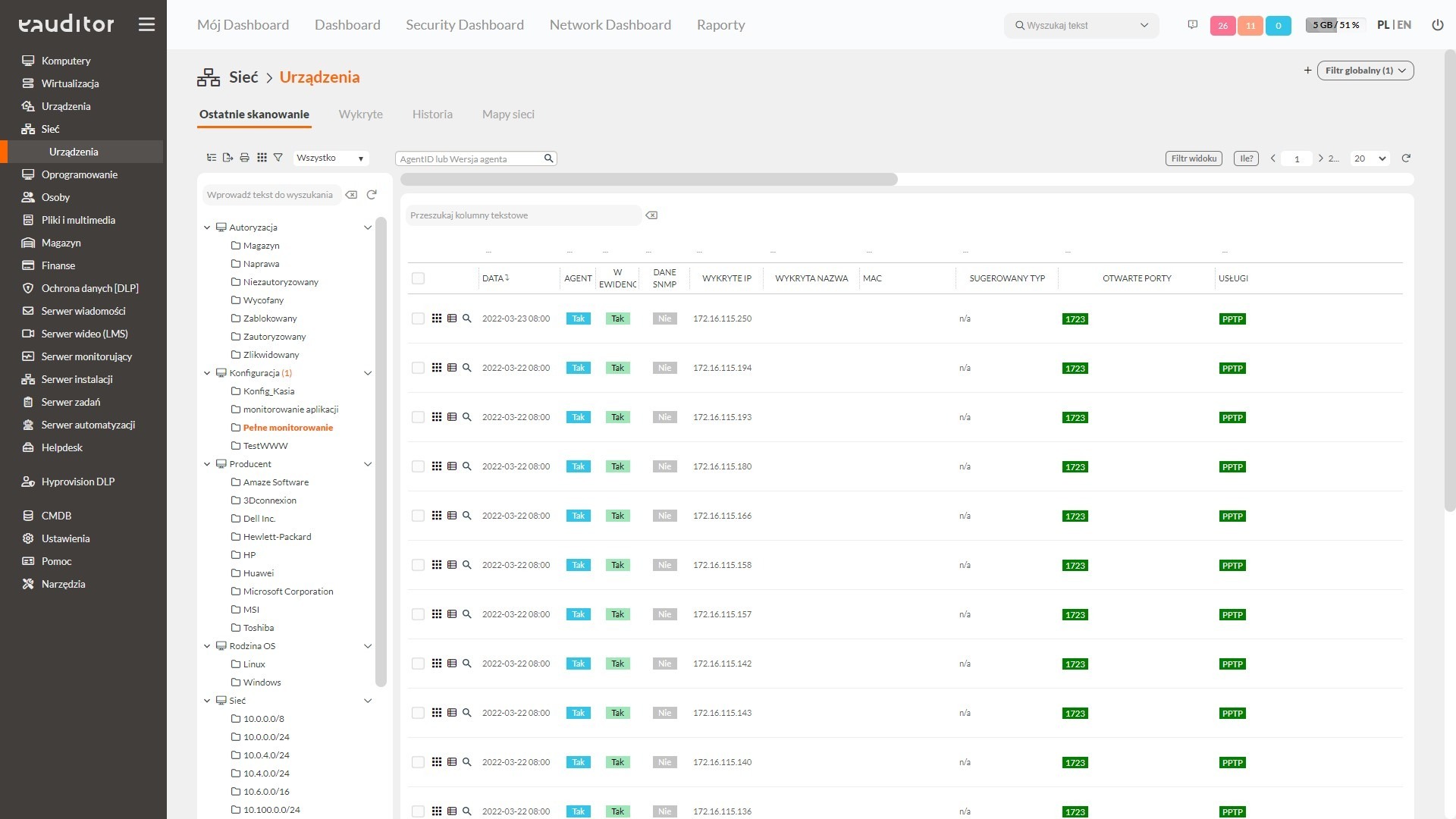
Network scanner functionalities
The scanner is a built-in functionality of the eAuditor system. It is located in the repository.
Functionalities of the eAuditor system network scanner:
- scanning devices by IP,
- scanning device ports,
- building network maps,
- building a list of services based on the ports they use,
- remote software installation based on WMI.
To access the commands that manage the scanner, select the checkerboard icon for general commands in the detected tab.
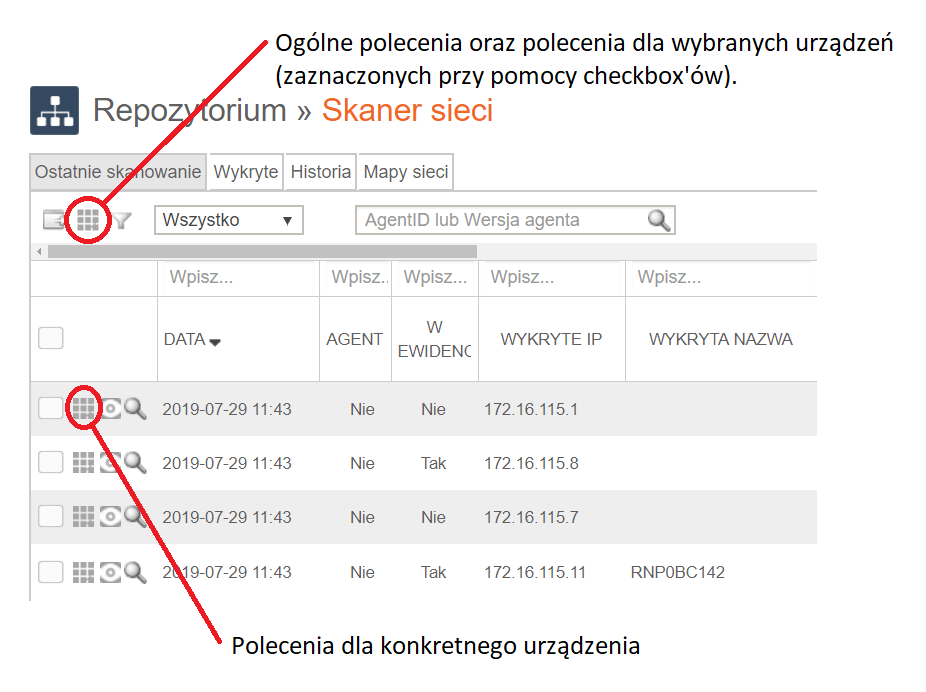
When you select the checkerboard icon, you will be presented with a window for selecting one of the following commands:
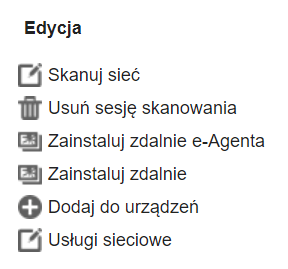
Scanning the network
To scan the network, select:
- the ports (services) on which the scanner is to listen,
- the range of IP addresses to which ICMP Echo Requests are to be sent,
- select whether to scan SNMP.
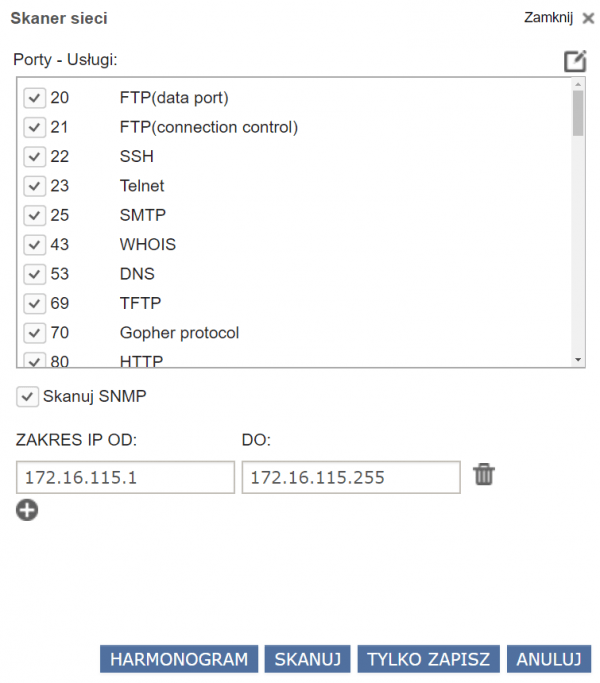
After making selections regarding IP ranges and ports of interest, it is possible to set up automatic scanning (according to a schedule). To set the schedule, select:
- frequency,
- the start date of the schedule,
- Determining whether the schedule is to be active.
After making selections regarding IP ranges and ports of interest, it is possible to set up automatic scanning (according to a schedule). To set the schedule, select:
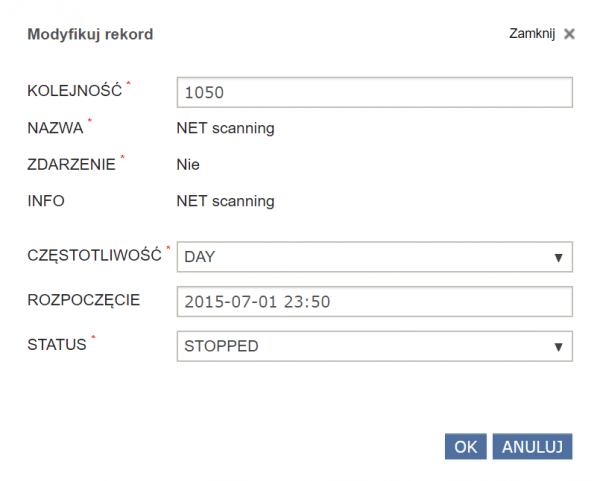
Deleting a scanning session
To remotely install the agent, use the “Delete scan session” option. When this option is selected, the entire actively visible scanning session will be deleted. For new scanning results, restart the scanner manually or wait for scheduled automatic execution.
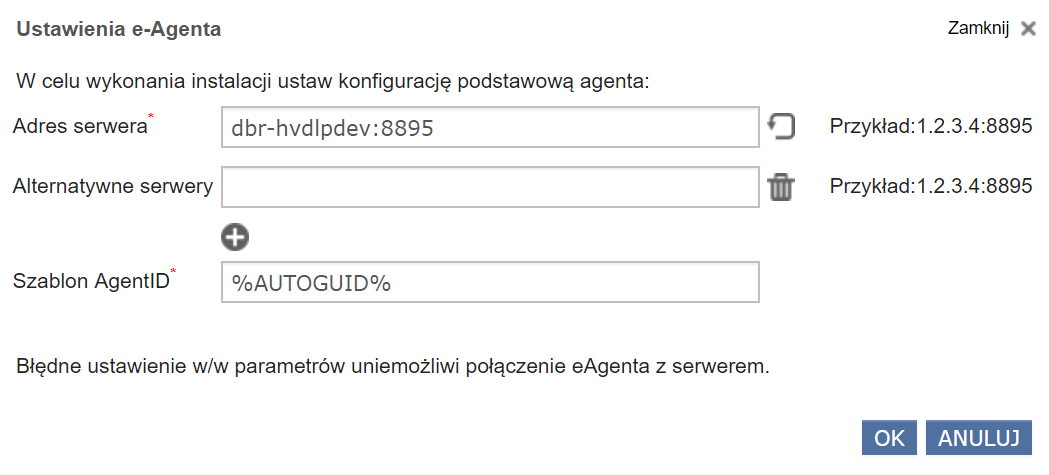
Remote installation of the agent
To install the agent remotely, use the “Install eAgent remotely” option.
The scanner has the functionality of remote installation of the eAuditor / Hyprovision system agent on computers connected to the network and having a supported operating system. Before remote installation, it is required to configure the computer accordingly. The entire process is outlined under “remote installation”.
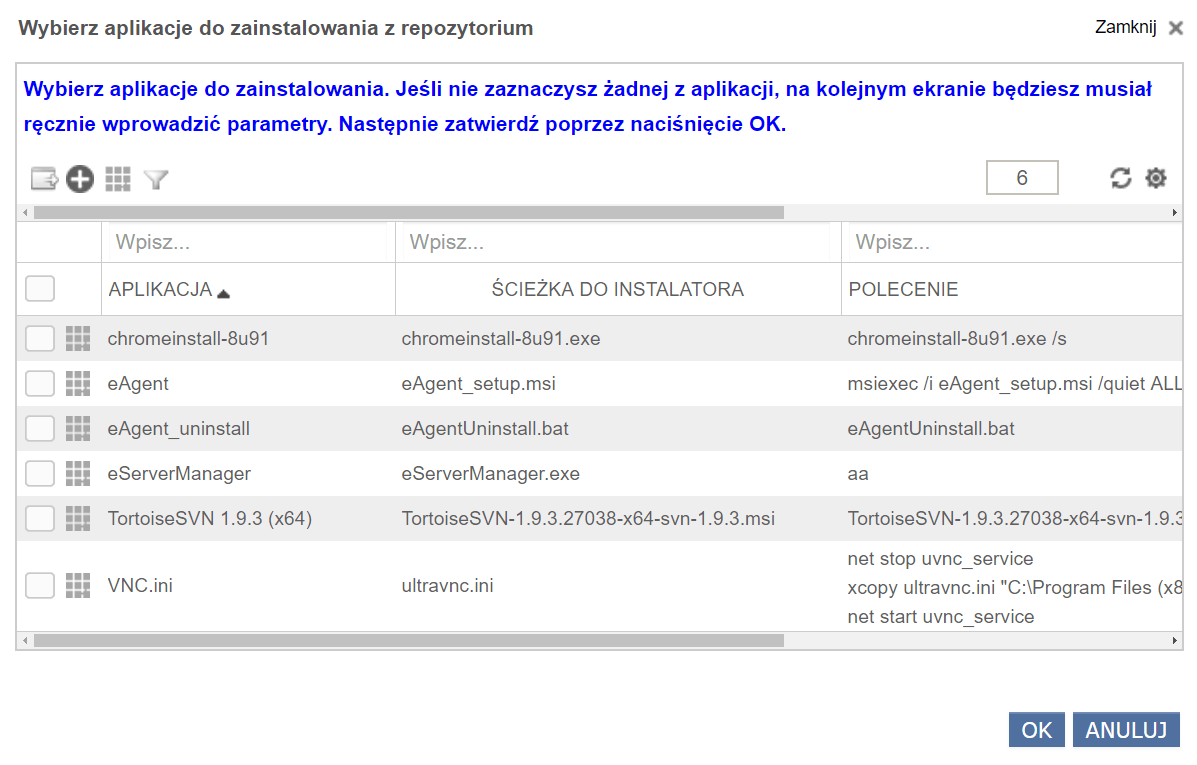
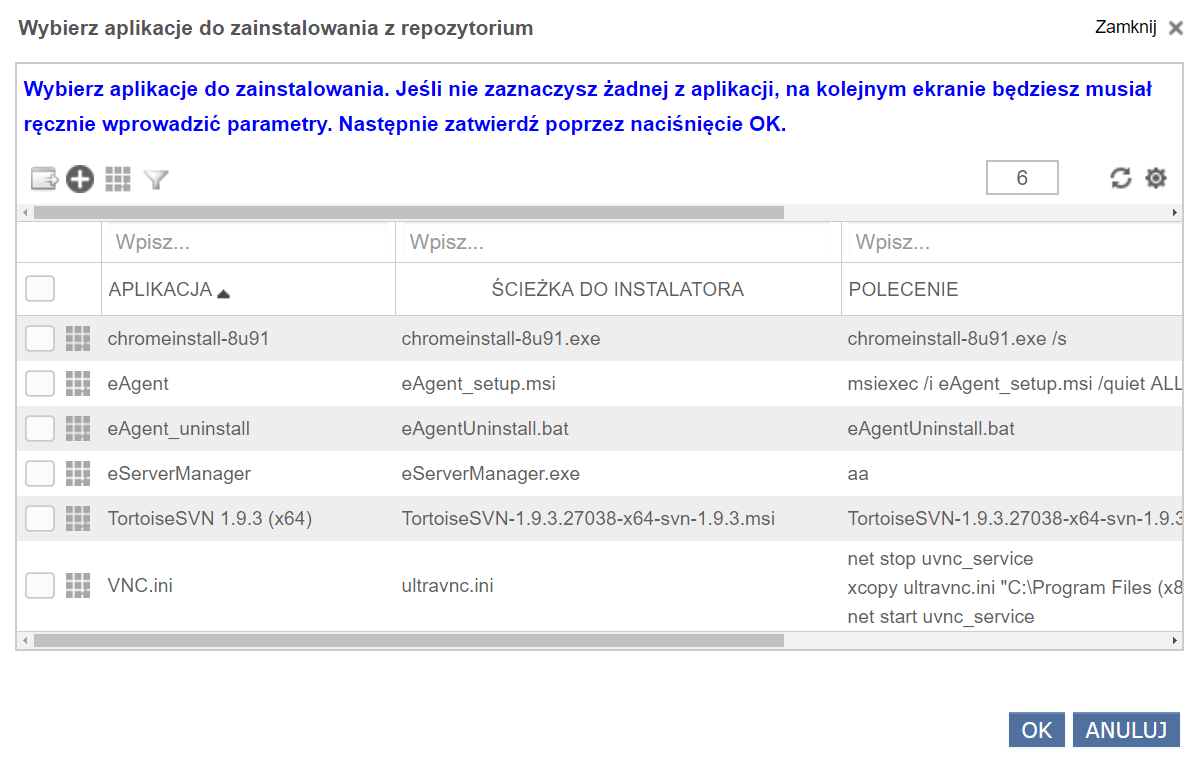
Remote installation of any software
To install the agent remotely, use the “Install remotely” option. The scanner allows installation of any software on computers (including those not equipped with an agent). To install the software on computers in our network, two conditions must be met:
the application must be in a repository on the server (it is possible to add any application to the repository),
The computer must have the appropriate system and the appropriate configuration as described under “remote installation”.
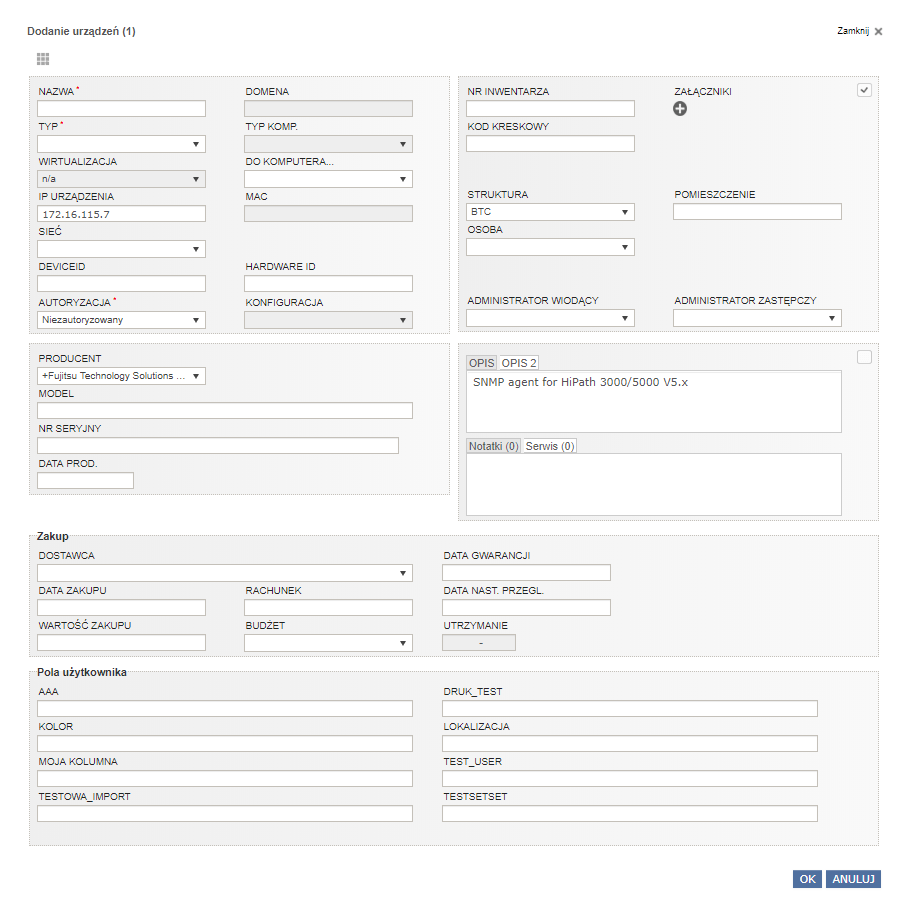
Adding to devices
From the scanner, we can directly add the found devices to the eAuditor system repository.
History
The history allows you to compare device activity including ports and services from any selected period in which the scan was performed. This allows you to see what services were active or inactive at any given time.

Network maps
A network map building function is built into the eAuditor system’s network scanner. There are 8 built-in maps:
- no problems (devices with no service issues),
- printers,
- offline computers,
- online computers,
- problems (devices with a service problem),
- switche,
- services.
In addition, the map has filters so that we can customize the view to our needs:
- zoom (from 20% to 400%),
- device status (offline, online or any),
- subnetwork,
- device type (printer, computer, router, switch, VoIP phone, n/a ),
- port/service,
- any search phrase.
Learn more about maps of the network.
Scanning devices on the network
The scanner scans all active and connected devices whose IPs are within the scanning range, so we are able to check if unauthorized devices are connected to the network. For this operation we do not need an agent installed on the computer. The scanner relies on broadcast-based sending of requests to computers.
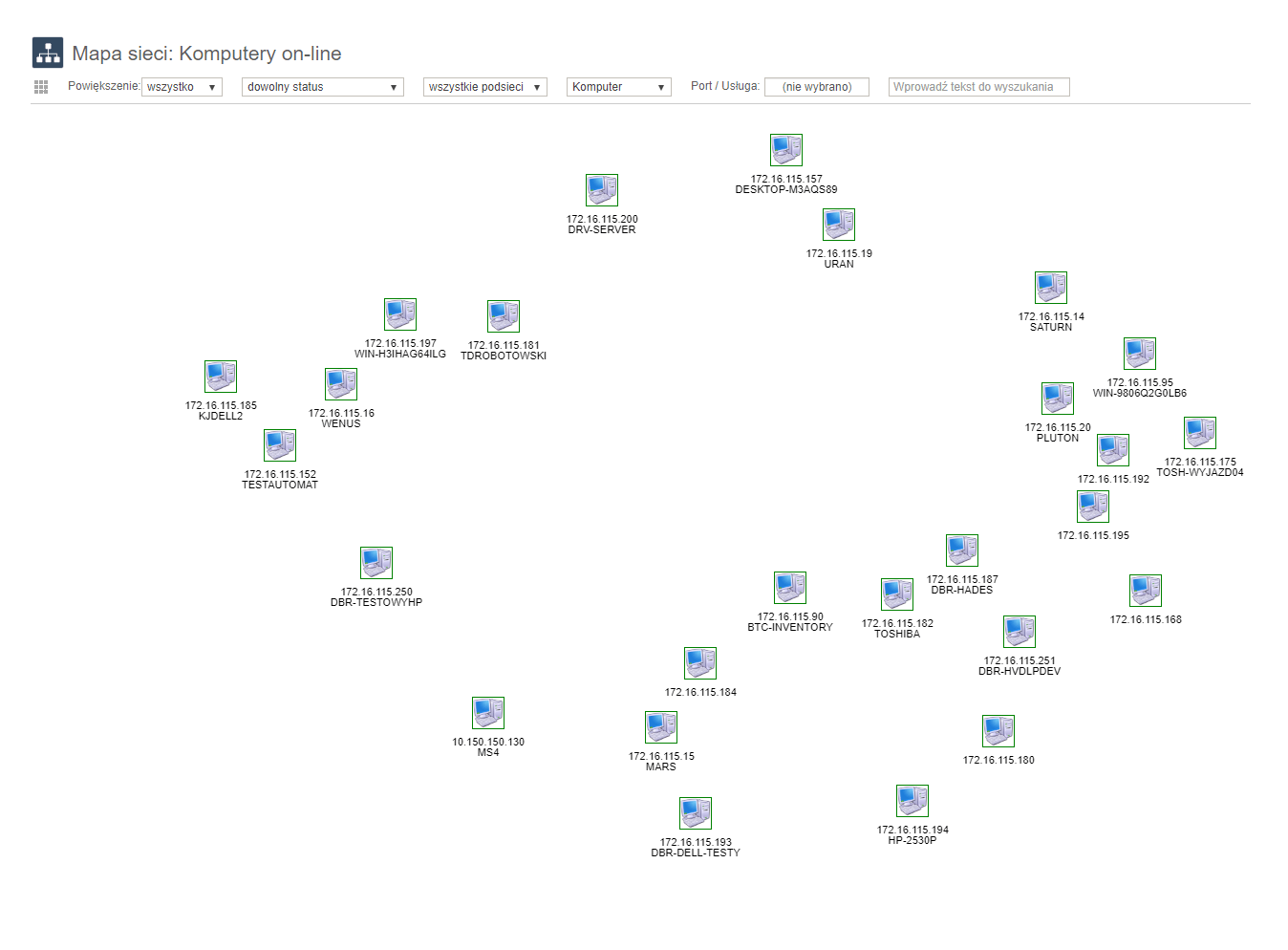
Scanning active services
Each service uses a specific port to communicate on the network. For example, the web server runs on the default port 80. By scanning active ports, we can determine what services are active on the computers in question. If you are monitoring a specific service, such as on a server, and the port is down, you will be prompted about problems with that service and it will be marked in red.

Monitoring of malicious or potentially malicious services/ports
It’s not just services or network protocols that use ports for communication.
What is a port really? Network port – an interface (logical) used for communication in a computer network. Internet protocols (UDP or TCP) packets pass in and out through it, using virtual ports as connection points for information exchange and data transmission. Data is sent from the port on the originating device and arrives at the receiving end of the line. (Wikipedia)
Anything we send to a computer network must use a computer port to transmit data, so in order to protect against data leakage, the first thing to monitor is the ports.
Potential malicious / unwanted applications / services that send data to the network:
- Applications like network games also work on specific ports.
For example, the game DOOM runs on port 666, so if we notice activity on this port, it is likely that an employee is using a computer game. - Instant messengers used to converse between users. If we don’t want data to be leaked, we should monitor the ports of instant messengers. For example, the TeamSpeak instant messenger uses port 8767.
- Peer to peer applications most often used to download files from torrent networks. For example, the BitTorrent application works on ports from 6881-6899.
The eAuditor system’s network scanner allows you to add your own ports for monitoring.
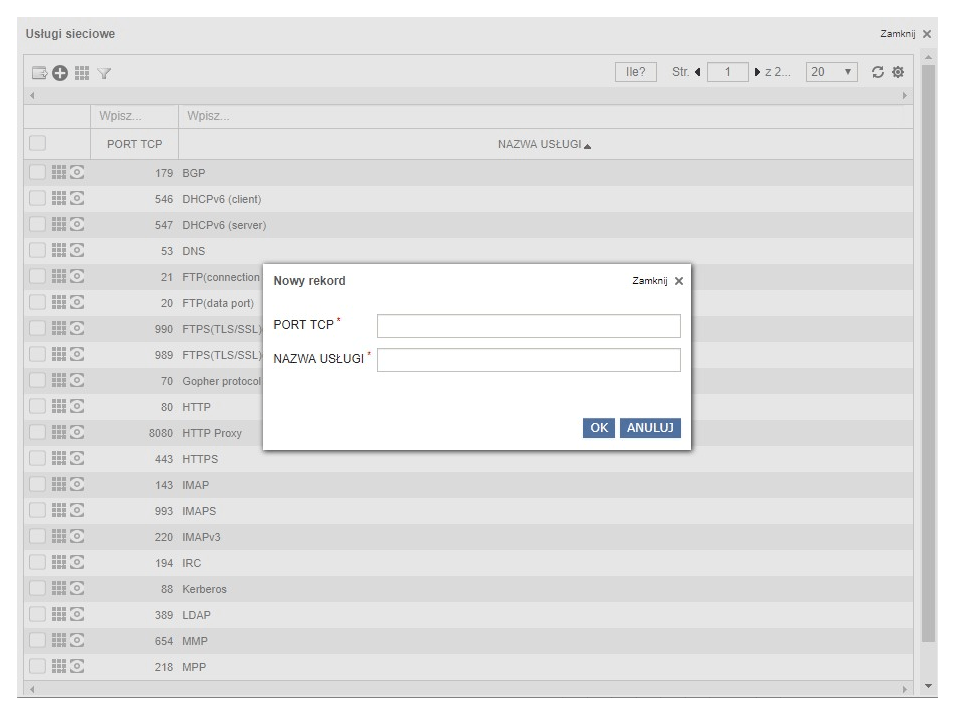
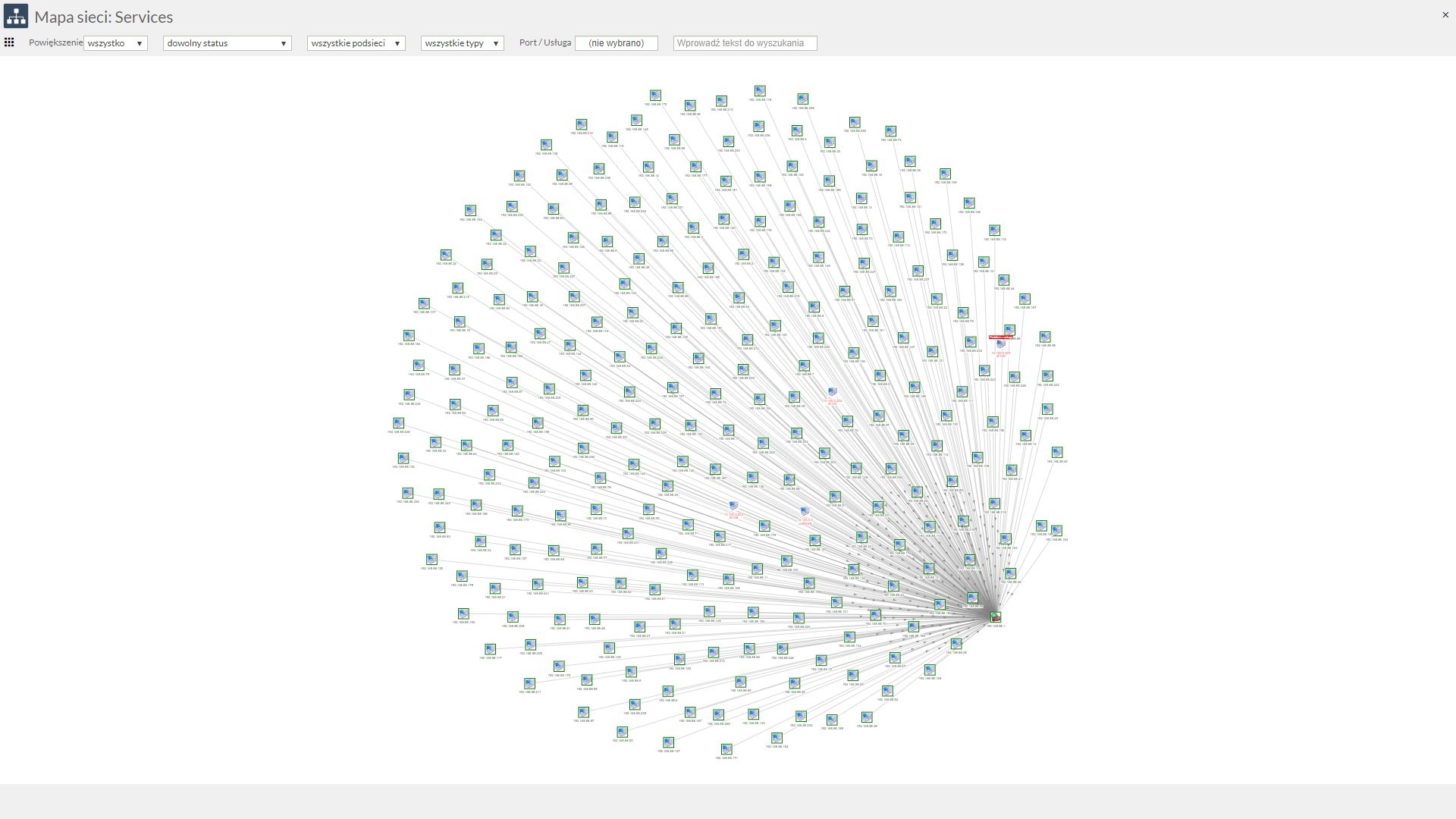
Building network maps
The network scanner allows you to build network maps by plotting the connections between computers, so you can graphically present – with the help of various filters – the structure of computer connections in the network (what topology they are in, etc.).
SNMP
What is the SNMP protocol? SNMP (Simple Network Management Protocol ) is a standard Internet protocol for collecting and organizing information about managed devices on IP networks and modifying this information to change the behavior of the device. (Wikipedia)
The eAuditor system’s scanner has SNMP protocol support, so we can check the current status of devices, such as switches (as long as it has SNMP protocol support), and we can get information such as:
- current status and the number of ports, which are up and which are down,
- network interface information:
– IP address,
– mask,
– MAC address,
– status (open/down),
– type,
– speed,
– number of bytes sent,
– number of bytes received. - port information of the network device such as:
– MAC address (of the plugged-in device),
– port status (open/down),
– type,
– speed,
– number of bytes sent,
– number of bytes received.

Remote installation
The eAuditor system scanner allows remote software installation using WMI.
What is WMI? WMI (Windows Management Instrumentation) – a set of Windows protocols and extensions that allow you to manage and access computer resources, such as network adapters, currently open programs, process lists. It also offers remote access to managed computer components. (Wikipedia)
Installation involves installing packages / applications found on the server repository. Remote access to WMI must be enabled for operations on each computer:
PPM on that computer> >Manage>> Services and Applications > >WMI Service Control >>PPM and then Properties >> Security.
From the directory tree, select “Root” and then security. Then set the “Remote Enable” permission for the selected user (administrator) or group and confirm the selection.
Configure the firewall to not block remote access. Start CMD as administrator and execute the following command “netsh firewall set service RemoteAdmin enable”.
UAC configuration:
We run CMD as administrator and execute the following command:
“reg add HKLMSOFTWARE/Microsoft Windows CurrentVersion /v LocalAccountTokenFilterPolicy /t REG_DWORD /d 1”.
Equipment inventory
The scanner provides information not only about IP addresses, open ports, addresses, but also the physical addresses of the network card (MAC). This is a physical address that is theoretically impossible to change. This allows us to inventory IT equipment based on their MAC addresses.
Quality control of LAN connections
The eAuditor system’s scanner collects information about the quality of the connection:
- response time of services (services) given in milliseconds, information such as:
– average response time,
– minimum response time,
– maximum response time. - The amount of information delivered (number of packets delivered, lost, and percentage.



