NIS2 #15: Two-factor authentication (MFA)
Securing cloud systems in accordance with NIS2 – the role of MFA and access control
NIS2 in a nutshell
With the new NIS2 directive regulations coming into effect, organizations need to adapt their IT security procedures to meet the stricter data protection requirements, especially in the context of cloud environments. A key aspect of compliance with the new regulations is the effective management of access to systems and data stored in the cloud. The eAuditor solution, with its two-factor authentication (MFA) feature, enables organizations to secure access to cloud resources, minimizing the risk of unauthorized access and providing greater control over IT infrastructure security in accordance with NIS2 requirements.
New security challenges
With the growing popularity of cloud services, companies need to be particularly wary of the new data protection regulations imposed by NIS2. The Cloud Security Alliance (CSA) in its report highlights that more than 60% of companies planning to deploy cloud solutions are concerned that the new requirements will increase the need for security investments. At the same time, Ponemon Institute research indicates that companies that employ advanced security measures, such as data encryption and regular audits, are less likely to suffer security breaches.
NIS2 requires companies to implement appropriate measures to protect data stored in the cloud, which includes monitoring incidents and assessing vendors for compliance. Effective cloud risk management is becoming a key component of cyber security strategies, especially for companies operating in critical sectors such as finance or digital infrastructure.
How to meet NIS2 requirements with eAuditor?
Two-factor authentication (MFA)
USE CASE
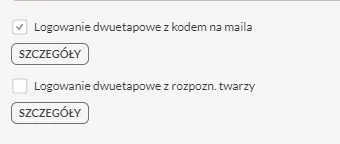
In connection with the implementation of the NIS2 directive, it was necessary to secure the eAuditor system by implementing two-factor authentication (MFA) at login. Responding to the requirements of Article 21 of the directive, the unit took measures to meet the requirements for access management and protection of critical IT systems.
Accordingly, it was necessary to prepare and implement a two-step method of logging into a critical system such as eAuditor.
To this end:
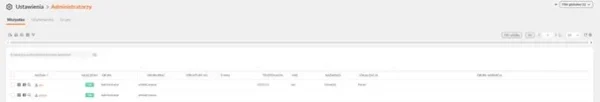
- In the eAuditor system console, user settings and logins were started.
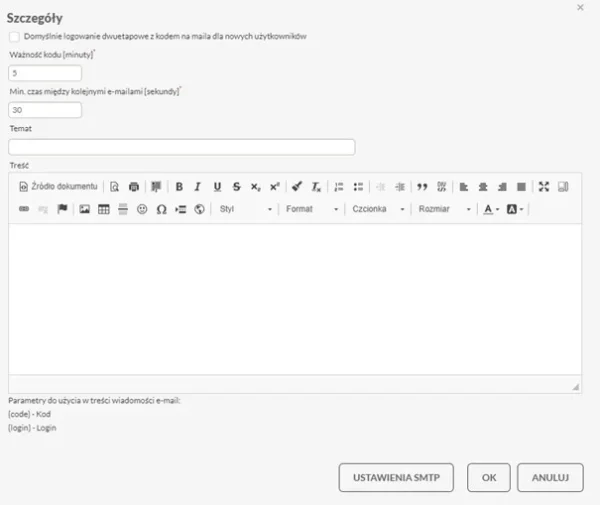
- Next, in the login settings options available under the icon – sprocket on the right side of the system window, login settings was selected, and then one of the available login options was selected.
- Once selected, the necessary server configuration was made to allow the system to interact with users, allowing the implementation of two-factor login to the system.
In the above way, the unit has raised its security standards by subscribing to the rules of the NIS2 directive.
Learn more about the software audit: https://www.eauditor.eu/uwierzytelnianie-dwuskladnikowe
NIS2 – Meet answers to questions
Q&A section
Due to numerous questions about NIS2, we have prepared a comprehensive list for you, in which we answer the most pressing issues related to the directive.
Question 1: What are the key requirements of the NIS2 directive to protect data in the cloud?
The NIS2 directive requires companies to implement appropriate data protection measures, including regularly monitoring security incidents, conducting risk assessments, and vetting cloud service providers for compliance. Particular emphasis is placed on data encryption, security audits and the implementation of access management mechanisms such as two-factor authentication (MFA).
Question 2: Is the implementation of two-factor authentication (MFA) mandatory according to the NIS2 directive?
No, the NIS2 directive does not impose a direct obligation to implement MFA. It does, however, recommend implementing appropriate measures to protect data and manage access to IT systems. MFA is one of the recommended security practices that significantly reduce the risk of unauthorized access. In practice, many organizations choose to implement it to meet the directive’s security requirements.
Question 3: Which industries are most affected by NIS2 regulations?
The NIS2 directive covers sectors deemed critical to the functioning of the economy and public security. These include the financial sector, energy, transportation, digital infrastructure, as well as cloud service providers and IT infrastructure, among others. Companies operating in these areas must prioritize the implementation of the required data protection measures.
NIS2 Essentials – useful links and resources
Want to learn more about NIS2 and the regulations that may affect your entity? We’ve put together the most important resources for you to help you better understand the upcoming changes.
- EU Parliament and Council Directive 2022/2025: Read the official NIS2 document
- The latest information about NIS2 on Biznes.gov.pl: Check what obligations you have to meet
- Directory of BTC systems that will help you comply with the NIS2 directive – Read -. https://www.eauditor.eu/dyrektywa-nis2-odpowiedz-unii-europejskiej-na-rosnace-cyberzagrozenia/
- Law on National Cyber Security System -. https://isap.sejm.gov.pl/isap.nsf/download.xsp/WDU20180001560/U/D20181560Lj.pdf
Ensure NIS2 compliance now and protect yourself from high fines and cyber threats that are becoming a daily occurrence in the business world!